The more access rights an employee has, the more possibilities they have to misuse or abuse privileges. According to the ENISA Threat Landscape 2021 report, a third of surveyed organizations suffered from privilege abuse by insiders during the period from April 2020 through July 2021.
That’s why establishing an appropriate level of privileged account management plays a significant role in ensuring your organization’s cybersecurity. In this article, we disclose how to effectively manage accounts with elevated privileges using privileged account and session management (PASM).
PASM: What is it and how does it work?
According to the Buyers’ Guide for Privileged Access Management from Gartner (subscription required), PASM is one of the four key elements of privileged access management (PAM), along with privilege elevation and delegation management, secrets management, and cloud infrastructure and entitlement management.

By implementing PAM best practices and using dedicated privileged access management solutions, you can get full control over privileged access permissions that any user in your network can gain: either with privileged accounts or with other accounts with temporarily elevated access permissions.

The key focus of PASM is protecting privileged accounts and sessions. Particularly, this approach helps to secure, keep under control, record, and audit all actions of privileged accounts.
PASM tools, in their turn, monitor and record sessions as well as secure and control passwords, allowing you to fully manage accounts with elevated permissions. Therefore, we can outline two main tasks for PASM solutions:
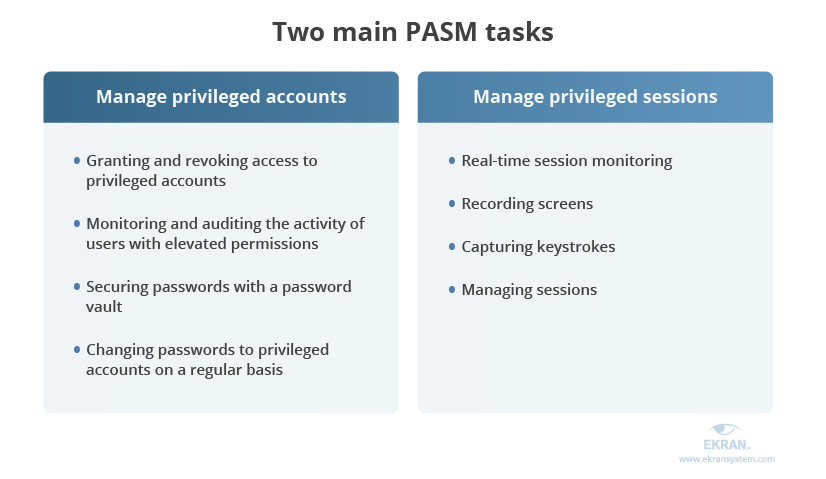
Let’s explore the specifics of both these tasks starting with privileged account management.
Managing privileged accounts
The first task of PASM is privileged account management. Its goal is to manage accounts with elevated permissions that allow access to critical data.
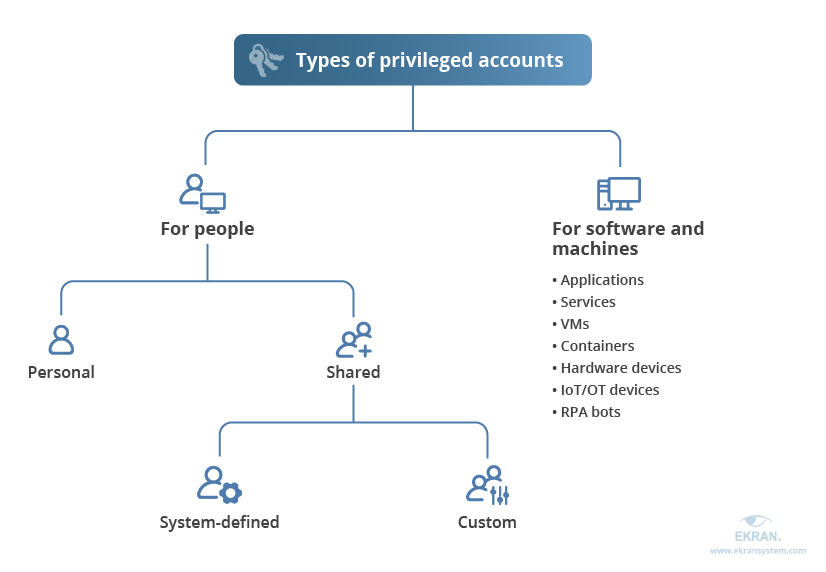
An organization usually has three types of privileged accounts:
- Administrative accounts
- System accounts
- Operational accounts
These accounts are one of the biggest risk factors within a corporate network. They’re vulnerable to both outsider attacks and insider threats and therefore need to be tightly managed.
Privileged account management includes:
- Granting and revoking access to privileged accounts
- Monitoring and auditing the activity of users with elevated permissions
- Securing passwords with a password vault
- Changing passwords to privileged accounts on a regular basis
Now, let’s look at the ways PASM can help you with keeping an eye on privileged sessions.
Managing privileged sessions
The second task of PASM is privileged session management (PSM), which focuses on sessions started by privileged accounts:
- Real-time session monitoring
- Recording screens
- Capturing keystrokes
- Managing sessions
PSM can help you identify unauthorized or anomalous actions and stop them until you can make sure that the controversial activity is legitimate. Plus, privileged session management provides an unimpeachable audit trail that proves rather helpful for incident investigation.
With PASM allowing you to manage both privileged sessions and accounts, you can address a large set of cybersecurity risks and boost the level of protection for your company’s critical information.
What Is Privileged Session Management And How Can It Help Secure Sensitive Data?
4 main reasons to implement PASM
One of the main goals of deploying a PASM solution or functionality for an organization is to ensure efficient privileged user activity auditing.
Administrator-level accounts are attractive to attackers who want to gain access to an organization’s critical data. Moreover, without appropriate management of privileged accounts, the possibility of administrators’ actions going undetected is much higher. So there are several reasons why your company should consider deploying PASM tools.
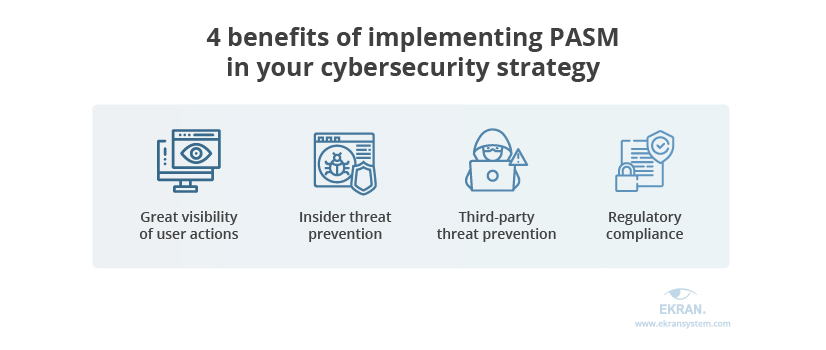
What can PASM give you?
- Great visibility of user actions. With PASM, you can watch every single privileged user session launched across both on-premises and cloud-based applications in a centralized location and in real time. Recorded session logs also show all details needed for internal or forensic investigations.
- Efficient insider threat prevention. Thanks to real-time visibility, you get a better chance of responding to an insider attack in a timely manner or preventing it from happening altogether.
- Robust third-party access management. A compromised subcontractor can become a weak point in a supply chain attack or can lead to operational, regulatory, and compliance risks. Cybercriminals can start with smaller targets to get to the data they want inside your organization.
- Seamless regulatory compliance. PASM capabilities are required for ensuring satisfactory incident response and proving regulatory compliance. In particular, adopting a PASM approach can help you meet the requirements of such laws, standards, and regulations as HIPAA, GDPR, SOX, PCI DSS, and ISO 27001.
Now, let’s take a look at actions that security managers can take to embed all main PASM capabilities into their organization’s data protection algorithms and determine core PASM features.
How to Pass an IT Compliance Audit
Making PASM work
How to deploy PASM inside your organization?
When implementing a PASM solution, you can look for a dedicated one that covers all your cybersecurity needs for the efficient management of privileged accounts and sessions. While different vendors offer different features, the core set of capabilities is usually the same. You can also build an effective PASM functionality by deploying several separate solutions.
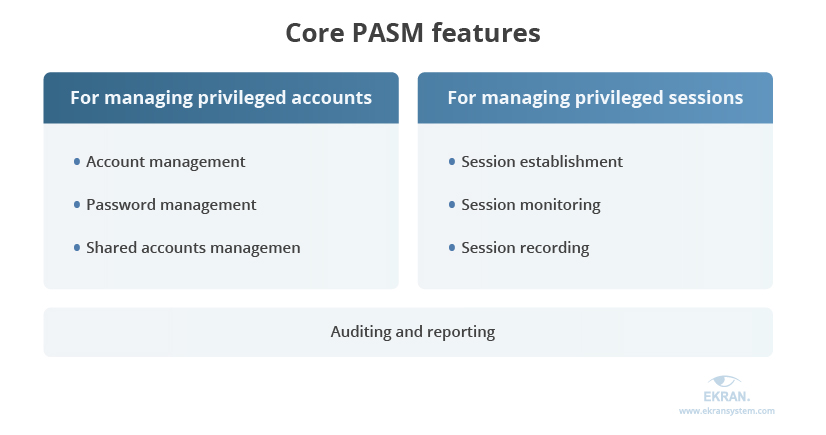
No matter the implementation scenario, there are five core PASM features that you should focus on to ensure proper protection and management of your organization’s privileged accounts. Let’s look closely at each of them.
5 key features of PASM solution
When selecting PASM functionality, pay special attention to the features it provides. Here’s a list of key PASM features you should look for:
Windows RDP Session Monitoring
1. Privileged account management
This feature helps you determine all accounts with elevated permissions on different types of devices. Thus, you can manage them effectively and disable, block, or delete accounts as needed.
When left unaccounted for and uncontrolled, privileged accounts pose a serious threat to your company’s security. PASM capabilities help you discover administrative-level accounts in systems and apps, create such accounts, and modify them based on your organization’s needs. You can also evaluate whether certain users need certain accesses for work and remove unnecessary ones.
2. Password management
Efficient password management capabilities will help you better protect access to privileged accounts and therefore secure sensitive data. These features help you vault passwords, as an encrypted and hardened vault is essential for storing privileged account credentials, including private keys and passwords.
Password rotation, where passwords are changed on a regular basis, is also a basic security element. It’s a common practice to change passwords at set intervals (weekly, monthly, or quarterly) or after specific events.
3. Shared accounts management
Some privileged accounts get shared permissions and thus should be controlled thoroughly. PASM features enable access control for shared accounts. Access may be granted based on additional workflow approvals or the use of high-trust multi-factor authentication (MFA) — a mechanism for all accounts with elevated privileges.
At least two-factor authentication is required for decreasing the risk of credential theft and improving the protection of your company’s sensitive data. A single sign-on (SSO) for shared privileged accounts is also needed for privileged sessions that are automatically established in a secure manner using protocols such as SSH, RDP, and HTTPS. In that way, actual credentials aren’t revealed to users. Using remote desktop monitoring software can help you implement this no matter where the users connect from.
4. Privileged session management
If your accesses are all secured, then the initial PASM features are set up. But to control all activity of privileged accounts, you need to closely watch all sessions launched by them. The main features required for doing this are:
- Session establishment, which helps you establish a separate session for each privileged user to ensure better visibility into their actions
- Privileged session monitoring, where a real-time view of sessions helps you not only closely monitor but also terminate suspicious activities or unauthorized sessions by dint of alerts and notifications
- Privileged session recording and playback, where all privileged sessions are recorded in a searchable and comprehensive way in both video and command-line formats
5. Auditing and reporting
A PASM solution should have comprehensive reporting features that can provide you with detailed information on privileged accounts and their activities. These features enable cross-checking of incident response activities and analyzing the landscape of cyber threats for a definite period of time. It provides detailed audit and video logs for both internal and external investigations, session analysis for researching suspicious events, and a report that includes all summarized activity.
Enhanced Reporting and Auditing
How to successfully adopt a PASM strategy?
We also have some recommendations for you to follow when implementing PASM in your organization:
Define corporate rules and policies for privileged accounts. Create a set of rules and policies for different types of privileged accounts that exist in your corporate network. Determine what groups of users can access critical information and what actions can be performed with particular privileges.
This way, you can effectively manage and control privileged activity within your corporate network. It’s best not to make just one privileged account in your organization, and it’s also a good idea to designate different privilege levels across the network for privileged accounts.
Deploy application-to-application password management (AAPM) to securely deliver credentials to applications and scripts.
Limit the scope of privileges. Apply the principle of least privilege, the zero-trust model, or the JIT PAM approach to give access or privileges only when and where needed. Consider denying full access by default and allowing privileged access on a case by case basis instead. Applying all these principles can help you make sure that users within your corporate network have only the necessary permissions and, as a result, can significantly decrease the risk of accidental data loss or leaks.
Don’t forget to educate your employees on cybersecurity risks. Human mistakes remain one of the biggest cybersecurity risk factors. Educate your employees on both your company’s security rules and the importance of following them.
For more useful tips on how to secure your privileged user accounts, read our post on local administrator account best practices.
Even though you can use separate tools for building your own PASM system, we suggest you put your time to better use and turn to an effective and affordable out-of-the-box solution – Syteca.
Zero Trust Architecture: What It Is, Benefits, and Key Principles
Implementing PASM with Syteca
Syteca is a full-cycle insider threat management platform that provides you with a large set of capabilities for implementing a compelling PASM strategy within your organization.
With Syteca’s lightweight privileged access management and privileged user management functionality, you can effectively manage access to sensitive data. Our platform also provides you with robust functionality for:
- Privileged user activity monitoring to enhance real-time session visibility and provide you with knowledge on every action taken by regular users, privileged users, employees, and third-party vendors
- Security event alerting, which enables you to notice abnormal activity and suspicious events in a timely manner, thus ensuring efficient incident response
- Powerful session recording, which keeps all screenshots of launched sessions and enables you to watch them in a YouTube-like video player
- Enhanced auditing and reporting, which gives you access to detailed audit logs and advanced report generation capabilities to help you learn all the details and discover the causes of privileged account abuse, privilege misuse, or inadvertent malicious activity
You can also use our platform as a Health Insurance Portability and Accountability Act (HIPAA), General Data Protection Regulation (GDPR), Payment Card Industry Data Security Standard (PCI DSS), or Sarbanes-Oxley (SOX) compliance software — which can help you keep privileged accounts under strict control and not only.
Conclusion
As part of privileged access management, PASM security focuses on privileged accounts and sessions. To implement this approach, you can leverage different tools for managing and auditing privileged accounts and privileged sessions for immediate threat prevention.
To deploy all core PASM features efficiently, you need to both set clear rules for working with privileged accounts and choose a comprehensive cybersecurity solution with the necessary functionality. With Syteca, you can successfully implement all core PASM features and ensure the proper protection of your organization’s privileged accounts.
Request a free 30-day trial of Syteca
and test its capabilities in your IT infrastructure!




