IT compliance requirements are designed to help companies enhance their cybersecurity and integrate top-level protection into their workflows. But passing an IT security audit can be challenging. Complex requirements, constant changes in standards and laws, and audit processes, and a high number of required security procedures are the key challenges of maintaining compliance.
The way out is with careful preparation and smart planning. By preparing ahead for an audit, you can enhance the security of your organization and achieve full compliance. Read this article to become fit and alert for your next IT audit.
What is an IT compliance audit?
An IT compliance audit is an independent evaluation of an organization’s cybersecurity tools, practices, and policies. An audit confirms that an organization meets the requirements of a certain regulation or law and is conducted by a certification body or by the organization that designs the standard.
To pass an audit and get initial certification, you have to contact the relevant IT compliance auditing authority, pay for the audit, and provide all the information required for evaluation. And as most compliance certificates expire, you’ll need to periodically repeat such IT audits to reaffirm compliance.
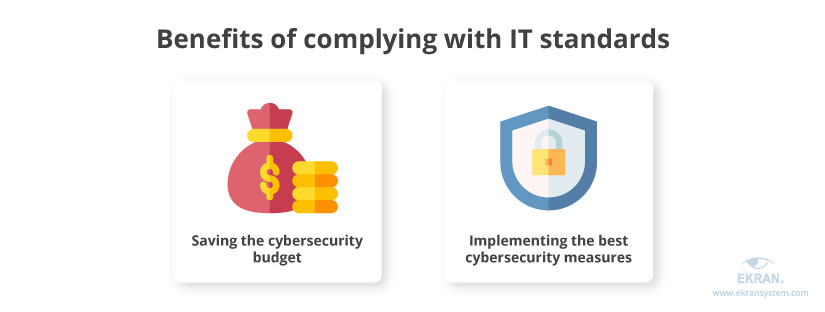
Compliance audits may seem complex and unnecessary at first, but passing them enables your organization to:
- implement the best cybersecurity measures. Standards contain both proven and cutting-edge methods to ensure security. Employing these methods can help you better protect sensitive data and avoid breaches.
- save your cybersecurity budget. According to The True Cost of Compliance with Data Protection Regulations [PDF] study by the Ponemon Institute, non-compliance with leading cybersecurity standards costs on average more than twice as much as maintaining compliance.
With that in mind, let’s discuss nine steps to smoothly pass any cybersecurity compliance audit.
Nine steps to pass a compliance audit
At Syteca, we work with organizations from various industries and study IT standards from all possible angles. Over the years, we’ve outlined nine universal steps that can bring a company up to security standards:
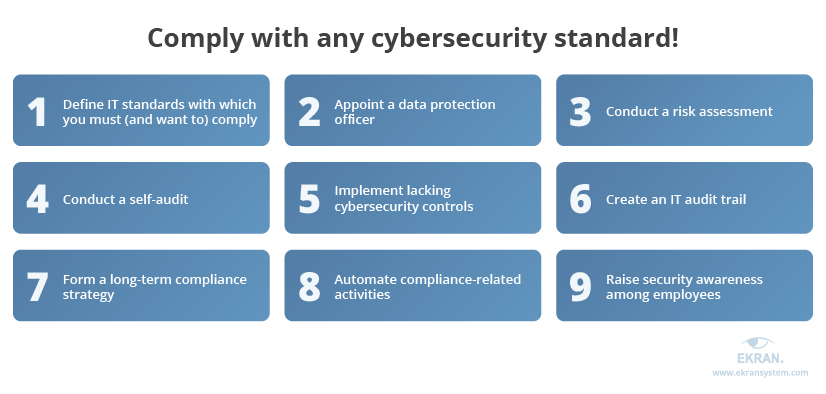
1. Define IT regulations with which you must (and want to) comply
Before you start improving your cybersecurity, you need to figure out which standards you must comply with and which you want to comply with voluntarily. Pay attention to obligatory and non-obligatory regulations, as both provide an organization with the benefits we discussed above. For example, ISO 27001 implementation is voluntary, but the demand for this certificate grows by the year according to the ISO Survey 2018.
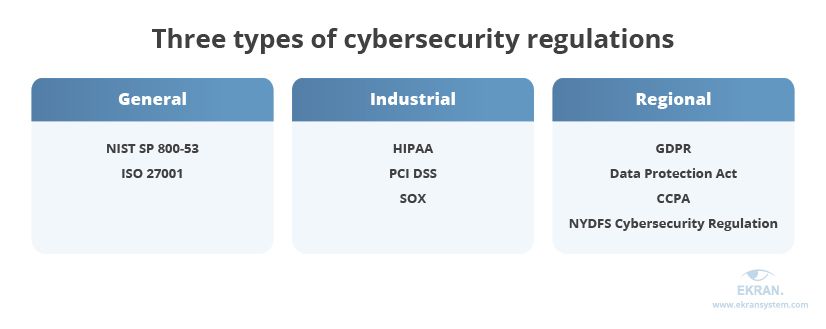
There are three types of regulations:
- General regulations apply to a wide list of organizations, regardless of their location or industry. Examples: National Institute of Standards and Technology (NIST) Special Publication 800-53, ISO 27001
- Industrial regulations apply to specific industries or organizations that handle specific types of data. Examples: Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standard (PCI DSS), Sarbanes–Oxley (SOX) Act, System and Organization Controls 2 (SOC 2). Thus, if your organization belongs to the healthcare or finance industry, you may be obliged to implement special HIPAA, PCI DSS, or SOX compliance audit software
- Regional regulations apply in particular countries, regions, or US states. Examples: EU General Data Protection Regulation (GDPR), EU Digital Operational Resilience Act (DORA), UK Data Protection Act, California Consumer Privacy Act (CCPA), New York State Department of Financial Services (NYDFS) Cybersecurity Regulation
The most obvious and safest way to figure out which audits do you need to pass is to consult with lawyers and cybersecurity officers. You can also analyze the data your organization handles to figure out which requirements it’s subject to. Usually, IT compliance focuses on three types of data:
- Personally identifiable information — Any information that relates to an identifiable person: name, home address, date and place of birth, biometric records.
- Protected health information — Results of medical examinations, information about health care plans, any medical records that can be linked to a specific person.
- Financial data — Credit card numbers, data on income and expenses, financial reports of an individual, organization, or any other entity.
7 Best Practices for Banking and Financial Cybersecurity Compliance
Once you figure out with which standards, laws, and regulations you need to comply, you can assign personnel responsible for compliance.
2. Appoint a data protection officer
A data protection officer (DPO) oversees data protection measures implemented in an organization, studies security requirements, and is responsible for meeting them.
Both the GDPR and PCI DSS require an organization to designate an employee who is responsible for compliance. But if you need to comply with other standards, laws, and regulations, appointing a DPO still brings several benefits:
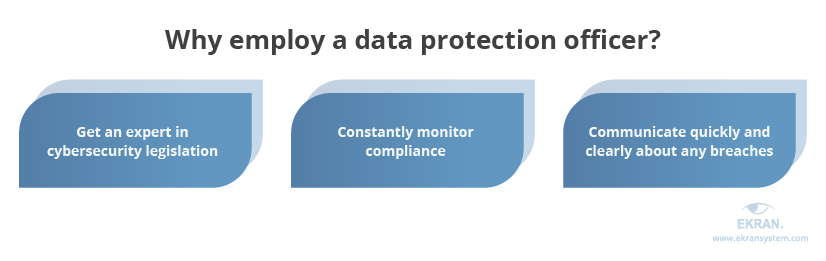
- Expert knowledge of cybersecurity legislation. According to the GDPR, a DPO has to prove their expertise in data protection and knowledge of corresponding laws, regulations, and standards.
- Constant monitoring of IT compliance status. While other employees focus on their responsibilities between audits, the DPO monitors changes in requirements, shifts in the organization’s cybersecurity, and the correspondence of current security controls to current cybersecurity requirements.
- Clear and fast communication about breaches. In case of a security breach, it’s up to the DPO to organize an incident response team, notify everyone affected by the breach, and report it to authorities and clients. A fast response to a security breach mitigates its consequences and reduces the amount of fines.
However useful a DPO may be, it’s important to remember that a single person can’t make an organization compliant. To help you pass an IT security audit, the data protection officer will require support from company management and the authority to improve existing security controls and policies, reconfigure existing software, and deploy new software.
NIST 800 53 Compliance Software
3. Conduct a risk assessment
A risk assessment identifies and analyzes security risks your organization might face. During a risk assessment, it’s important to identify:
- cybersecurity risks and threats to your organization
- assets that are critical to your organization and are subject to compliance regulations
- your current level of protection, as well as the weak and strong points of your defenses.
A risk assessment helps you grasp the state of your company’s cybersecurity. More importantly, it puts a number on the risks, allowing you to analyze how they may harm your organization. That’s why this process should be repeated periodically: you have to evaluate and assess risks at least once a year.
The results of a risk assessment will be useful for planning security improvements as well as for designing new policies and strategies.
Mitigating Insider Threats: Plan Your Actions in Advance
4. Conduct a self-audit
A self-audit has a lot in common with a risk assessment: it’s an evaluation of implemented security controls. But unlike a risk assessment, a self-audit helps you evaluate your current compliance level and identify gaps in data protection. It also prepares your employees for a real IT audit.
To conduct a self-audit and make it look more like a real audit, use official IT compliance audit checklist and guidelines:
- NIST assessment and auditing resources
- GDPR checklist for data controllers
- HIPAA compliance checklist
- And so on
The one big drawback to self-audits is their rather high cost, both in terms of money and time. However, discovering gaps in cybersecurity during an actual audit has an even higher cost: failing the audit and starting over.
5. Implement lacking controls
As a result of a risk assessment and self-audit, you’ll have a list of policies, practices, and technical controls you have to implement in order to pass an IT audit. Now you need to implement them.
Requirements of the most widespread regulations, standards, and laws have a lot in common. For example, most require implementing tools for identity management, access control, user activity monitoring, and breach notification.
To simplify and speed up the implementation of required controls, it’s best to deploy solutions such as Syteca that combine several security functionalities.
6. Create an IT audit trail
An IT audit trail is a set of records that depict any activities with sensitive data, databases, applications, or parts of your infrastructure. It allows IT compliance auditor to examine the way your employees handle sensitive resources and is an important part of any compliance and security audit.
Logging an audit trail is also useful for security monitoring and incident investigation. Using the generated logs, you can track any action inside your protected environment, identify security incidents, and assess threat sources.
Ensure that you record such a trail by deploying a user activity monitoring solution. It should log all user actions, store them in a protected format, and provide proof of malicious activity. Monitoring records are also useful during forensic activities and investigations.
7. Form a long-term compliance strategy
Compliance audits happen regularly, which means you constantly have to review and improve your security measures to stay compliant. That’s why you need to create a compliance strategy — a set of internal policies and procedures that will help your organization stay compliant.
It’s important to form this strategy with a deep understanding of the workflow of each affected department so as not to have an adverse effect on established processes. Therefore, work closely with leaders of all departments, allowing them to provide direct input and suggestions.
Once your compliance strategy is complete, it’s important to assign people responsible for its implementation. Usually, a data protection officer or chief security information officer is in charge of this strategy.
8. Automate compliance-related activities
Some activities during the compliance audit have to be performed manually: reviewing policies, investigating security incidents, cooperating with a certification body, etc. Still, automated tools help you reduce compliance overhead, save time preparing for the audit, and minimize the risk of human errors.
With dedicated NIST 800-53, GDPR, HIPAA, SOC 2, or PCI DSS compliance solutions, you can automate:
- continuous security monitoring
- implementation of access management policies
- alerts and notification on suspicious events
- collection of data for audits
- reports generation.
Automation is especially helpful for large organizations that have to pass several IT compliance audits annually.
7-Step Checklist for GDPR Compliance
9. Raise security awareness among employees
Passing an audit requires all employees working with sensitive data to understand their responsibilities and use safe practices. Sometimes it means they have to adjust or change their work routines, which is not always welcomed.
To help employees understand their role in the audit process, you can:
- explain how data leaks and failed audits will influence the organization
- share information on security breaches in your industry
- conduct cybersecurity trainings
- communicate the importance of new security controls
- describe the outcome of non-compliance.
Your goal here is to create a shared understanding of the reasons and importance of enhancing cybersecurity and passing an audit.
To learn more about security standards and preparations for audits, check out our blog. In our articles, we discuss specifics of industrial security standards as well as ways to improve corporate cybersecurity and ensure compliance using Syteca functionality.
Conclusion
Passing an IT security audit is a challenging but essential part of building and maintaining a strong cybersecurity system. But with the right security tools, this process becomes much easier.
Syteca is an all-in-one cybersecurity platform that allows you to enforce user monitoring, identity management, and access controls as well as to detect and react to security incidents. Our platform helps organizations align their cybersecurity practices with a wide list of IT compliance requirements.




