Privilege abuse is the top misuse-related reason for data breaches according to the 2021 Data Breach Investigations Report by Verizon. To mitigate the risk of data leaks and other incidents, it’s crucial to enhance the protection of critical assets and keep a close eye on the activity of privileged users.
Yet it can become a real ordeal for an IT security manager not only to secure access to their organization’s servers but also to track and manage all privileged sessions. In this article, we discuss the importance of privileged session management (PSM) and explore how it can help organizations enhance the security of sensitive data.
The role of PSM in data security
During privileged sessions, users with elevated access rights interact with the organization’s sensitive data and critical systems. Having a strategy for managing privileged users and accounts is the right way to prevent and immediately detect threats. To minimize the risks of data breaches and data leaks, security teams often adopt PSM.
What is privileged session management?
Privileged session management is the process of monitoring, controlling, and recording sessions initiated by privileged accounts. Session recording provides visibility into how users interact with sensitive data, which helps with investigating data crime and meeting compliance requirements. Also, PSM software usually offers alert functionality that helps the security team to immediately detect and respond to cybersecurity events.
How does privileged session management work?
Now that we know the definition of privileged session management, it’s time to consider the three major tasks it helps you accomplish:

Monitor privileged activity. Monitoring privileged activity from account login to logout is essential to determine who accessed a particular asset, where, why, and when.
Alert on potential threats. Getting timely notifications on suspicious activity is crucial for fast and efficient detection of potential threats and response to cybersecurity incidents within a privileged session.
Record privileged sessions. Having full records of all privileged sessions creates an audit trail to identify unusual or suspicious behavior, operational and system implementation issues, or system errors. It creates an audit log that is also needed to ensure compliance with cybersecurity requirements and can be helpful for further forensic investigations.
User Activity Monitoring Alerts and Notifications
Let’s now take a closer look at the specifics of privileged sessions themselves and reveal who initiates them, how, and why.
The two most common types of authentication protocols for privileged sessions are:
- Secure Shell (SSH) — grants access to Linux or any other operating system servers and is intended for technical specialists, with key encryption that is difficult to crack
- Remote Desktop Protocol (RDP) — grants access to Windows virtual machines and physical servers and is commonly used by employees of all technical levels
Secure Socket Shell (SSH) Key Management: Overview & Best Practices
Privileged sessions can be launched by different users: consultants, administrators, employees, vendors, engineers, and other actors. We can outline three groups of users who can start privileged sessions based on how they access an organization’s internal network: on-premises, in the cloud, or remotely (for authorized third-party users).
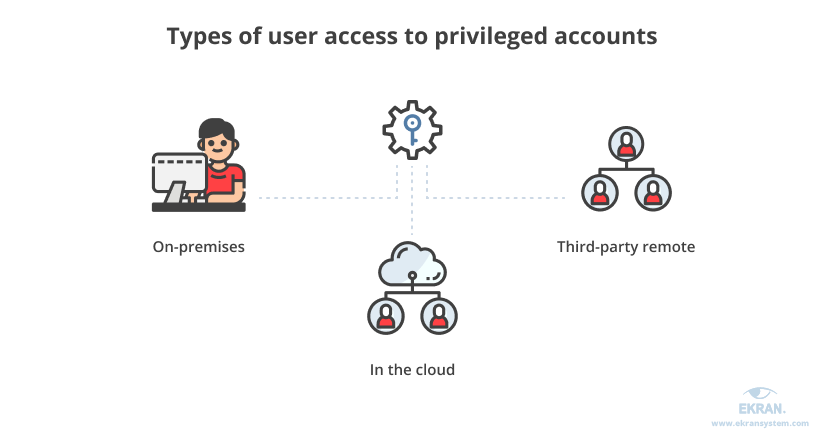
Finally, there are different tasks that users fulfill during privileged sessions. For example, admins might initiate privileged sessions to set and adjust the configurations of critical systems or applications, remove or add users, or delete specific data. Maintenance engineers use privileged accounts for software patching, troubleshooting, and other fixing processes. Third-party vendors and consultants can also use privileged sessions to access an organization’s marketing, financial, or human resources systems.
PSM vs PAM vs PASM
It’s sometimes easy to confuse PSM with other approaches related to privileged activity management, like privileged account and session management (PASM) or privileged access management (PAM). Let’s briefly explore the differences between them and discuss the main security tasks behind each approach.
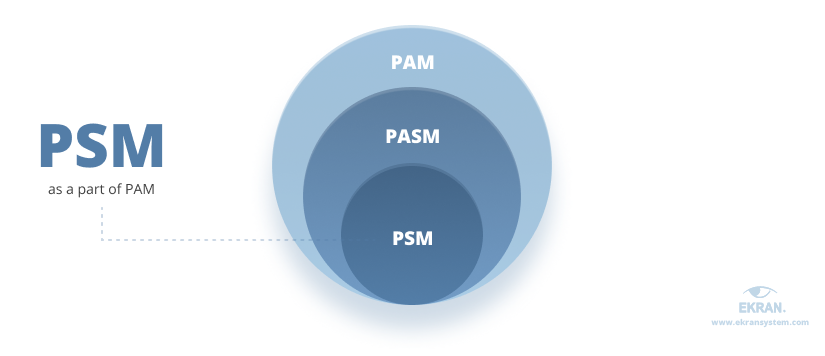
Privileged access management (PAM) is a comprehensive security strategy for controlling, managing, and monitoring privileged access to an organization’s critical systems and data. Not only privileged accounts can gain elevated access rights; unprivileged (non-administrative) accounts can as well. For instance, regular employees can access sensitive data if such access is needed for work on a specific one-time request.
Privileged account and session management (PASM) is a part of PAM that manages credentials and sessions of privileged accounts.
Unlike PAM and PASM, privileged session management means fully tracking, controlling, and accounting for activities only within an ongoing privileged session, enabling you to pinpoint threats inside the activity of high-risk accounts.
Now that we’ve distinguished among these terms, it’s time to discuss the benefits of implementing PSM in your organization’s cybersecurity.
Privileged Access Management (PAM) Solutions
Why do you need PSM?
Organizations face numerous cybersecurity risks that properly established privileged session management can help mitigate. Here are the three common cybersecurity risks that can come from insufficiently managed privileged sessions:
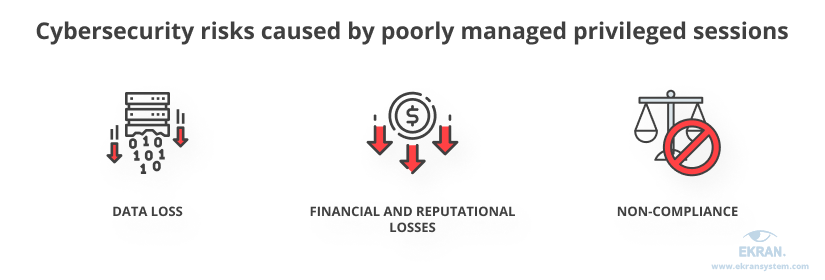
Data loss. Privileged sessions are often used to access sensitive data and critical systems. Failure to closely monitor and control such sessions can lead to malicious actors compromising or stealing data important to your organization. Privileged session management helps you detect and stop potentially dangerous user actions before they lead to a cybersecurity incident.
Financial and reputational losses. Dispersed and unsupervised privileged sessions compromise the security of both an organization and partners that use its services or products. The chances for data leaks and other cybersecurity incidents increase if proper privileged session management is absent. Thus, an organization can suffer from reputational losses, loss of customers’ trust, and additional expenses on penalties, fines, and lawsuits.
Non-compliance. Not meeting compliance requirements can lead to expensive fees, and in some cases even imprisonment for criminal negligence. For instance, disclosing individually identifiable health information can be punished with imprisonment according to HIPAA rules. Not implementing mandatory services and practices to protect sensitive data can also lead to loss of customer trust. PSM, with its capturing of all on-screen activities, helps organizations keep an eye on how users handle critical assets, which is required by various cybersecurity laws, standards, and regulations.
Meeting IT Compliance Requirements
Apart from enhancing data security and helping your organization comply with cybersecurity requirements, implementing PSM can bring the following benefits.
What is PSM security aimed at?
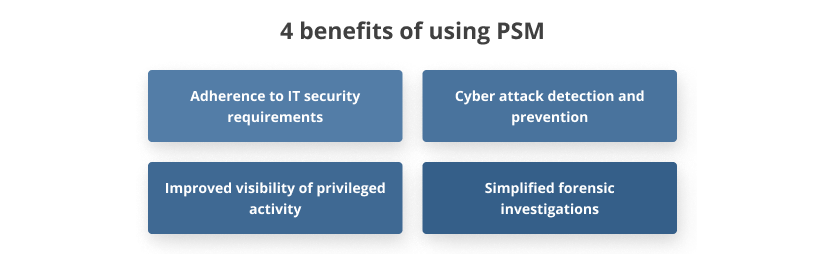
Adherence to IT security requirements. Leading cybersecurity requirements pay lots of attention to monitoring the activity of privileged users. Privileged session management can help you meet the requirements of many standards, laws, and regulations, including:
- The Gramm–Leach–Bliley Act (GLBA)
- The Sarbanes-Oxley Act (SOX)
- The Health Insurance Portability and Accountability Act (HIPAA)
- The Payment Card Industry Data Security Standard (PCI DSS)
- The Federal Information Security Management Act (FISMA)
Cyber attack detection and prevention. With session monitoring and a security incident alert system, it’s simple to quickly detect how attackers access and use your system as well as to react to any malicious or strange actions. You can stop a suspicious session manually after seeing an alert, or you can configure automated session blocking and incident recording.
Improved visibility of privileged activity. With a PSM functionality, no sessions can remain out of sight or uncontrolled. During real-time privileged user monitoring, it becomes obvious who has no need for privileged access and can use it to jeopardize a business. Recorded sessions can also help to detect data leaks caused by current employees or even former employees whose access permissions weren’t revoked. Based on data received from those records, IT administrators can revise the current security policy. Visibility of users’ mistakes makes it easier to analyze, work through, and avoid these mistakes in the future.
Simplified forensic investigations. In case a cybersecurity incident occurs, a tool with PSM capabilities provides you with audit logs that help uncover all steps taken by a user of a privileged account. Knowing dates, times, and other details will help you understand the full context of a particular event. Recorded sessions are a necessary addition to the visualization of all user’s steps in internal or external investigations.
Without appropriate PSM functions available in your cybersecurity solution, it is extremely difficult to detect threats and vulnerabilities inside local or remote IT systems. You may need a robust platform for VDI monitoring, such as Citrix or Amazon WorkSpaces monitoring tool, that includes functionality for keeping privileged sessions under control.
How to Protect an Enterprise Database from Privilege Abuse
How to manage privileged sessions with Syteca
Syteca is a comprehensive insider risk management platform that can help your company effectively navigate the modern threat landscape.
Among all the rich functionality that you get by deploying Syteca is a set of identity management and PAM tools for detecting threats at all levels. Inside our PAM solution, you’ll likewise get complete PSM functionality.
Let’s explore how exactly Syteca can help you solve the three tasks of PSM we discussed above.
Monitor privileged sessions
Syteca’s user activity monitoring (UAM) is a powerful tool to monitor the activity of regular and privileged users, from inputting credentials right until the end of the session.
You can granularly configure monitoring for different user groups and review all user sessions in real time. For example, you can monitor activity of all privileged users, including your employees and third-party vendors.
During every monitored session, you can see active windows, websites, applications, connected devices, titles, URLs, executed scripts and commands, and typed keystrokes.
With this functionality, it’s much easier to have control over all launched sessions from one place. As Syteca also provides Azure virtual desktop monitoring and Windows RDP session recording, centralized access is provided both to geographically sequestered assets and to privileged remote users no matter where on the globe they are.
Alert on potential threats
You can use Syteca’s security incident investigation capabilities to set alerts that will help you instantly respond to cybersecurity incidents.
For detecting and monitoring suspicious user behavior, Syteca also provides an AI-based user and entity behavior analytics (UEBA) module that can help you catch and stop dangerous inadvertent or malicious actions before they cause trouble.
Syteca enables both automated and manual responses to suspicious actions detected during privileged sessions. After receiving an alert, you can terminate or at least halt an unauthorized session or suspicious activity. You can also configure Syteca to automatically block or terminate a user, process, or application that launches an alert. Syteca offers ready-to-use alerts in its library and provides the opportunity for you to customize alerts.
7 Cybersecurity Challenges to Solve with UEBA
Record privileged sessions
As a comprehensive insider risk management platform, Syteca also offers user session recording functionality.
Each recorded session is accompanied with text metadata for on-screen activities, input and output audio streams, and important details on connections and remotely connected users. Thus, you can easily search for the necessary details within a chosen session and find information with only a few clicks.
Aside from these three main tasks, Syteca can help you comply with such laws, standards, and regulations as HIPAA, PCI DSS, SOX, FISMA, NIST, the GDPR, and GLBA. You can easily share an immutable audit log with auditors to prove that you are monitoring and capturing all privileged account activity as well as securing your sensitive data in other ways.
Conclusion
Privileged session management focuses on three things: monitoring tasks, recording them, and alerting on detected suspicious events. Implementing privileged session monitoring correctly helps you comply with IT security requirements and prevent data loss. Tracking user activity and recording sessions is an indispensable part of this to capture evidence that plays a central part in forensic investigations. Timely alerts help you respond to any incident quickly and reduce the number of cybersecurity incidents.
Syteca addresses these needs by implementing features of privileged session management inside its PAM functionality. Our up-to-date and lightweight technical solutions can help you simplify insider risk management and secure your privileged sessions from cybersecurity threats.





