For any organization, insider attacks are like a severe illness: prevention is better than the cure. Like illnesses, insiders mask their malicious actions and can harm your organization for a long time before you detect them. This harm can be in the form of a loss of data, customers, money, etc.
Planning a risk mitigation process helps to stop insider attacks at the early stages or reduce their potential damage. In this article, we discuss how to mitigate insider threats, why it’s worth doing, what the key steps are in this process, and how Syteca can assist you with risk mitigation.
How to plan your insider risk mitigation process?
Insider risk mitigation is the process of prioritizing, evaluating, and implementing risk-reducing controls and countermeasures in order to prevent insider-related risks or reduce the damage they cause.
Mitigating risks helps organizations detect and prevent insider threats that can lead to the realization of insider-related risks. The most common risks are loss of customers, reputational damage, and fines and penalties for non-compliance with cybersecurity laws, regulations, and standards.
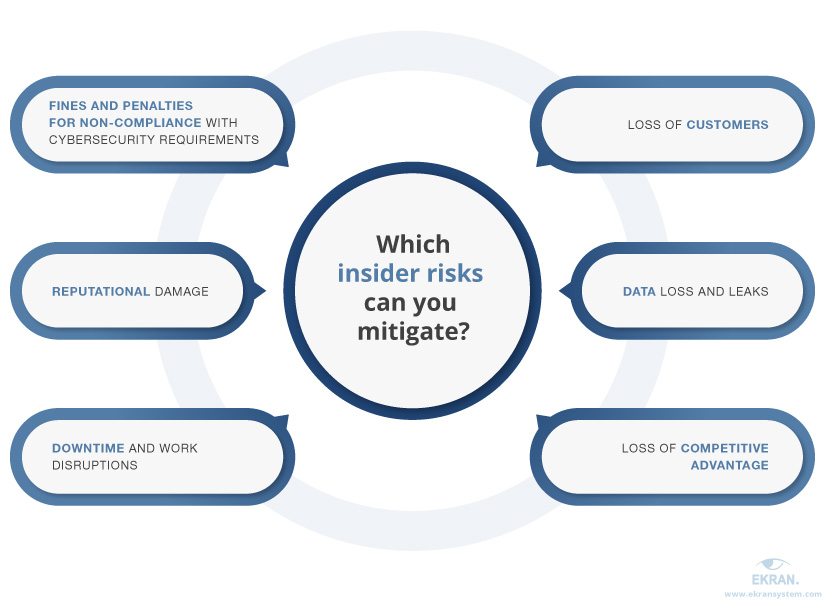
Acknowledging and proactively managing these insider risks allows organizations to avoid them or at least greatly reduce possible damage from malicious insider activity.
To be able to do that, you need to prepare a risk mitigation plan. Its preparation may be a separate process resulting in the creation of a standalone document or a part of building an insider threat program.
How to Build an Insider Threat Program [10-step Checklist]
Four components of an efficient insider risk mitigation plan
Mitigation activities are usually laid out in an insider risk mitigation plan — a document that maps out options and actions to reduce the impact of a risk if it becomes reality.
The key things to include in this plan are:
- Steps of the mitigation process. Usually, these include evaluating insider risks, prioritizing risks, and implementing mitigation controls. We’ll cover these steps later in this article.
- High-level mitigation insider threat mitigation strategies. There are five key risk mitigation strategies: acceptance, avoidance, transfer, control, and monitoring. When developing a risk mitigation plan, pick one of these strategies for each risk that your organization faces based on the risk’s probability and severity.
- Risk-reducing controls. You can implement controls such as new organizational activities, cybersecurity policies and software, and changes to existing procedures. An insider risk mitigation plan should fully describe these controls, the results the organization expects to get from them, and employees responsible for their implementation and supervision.
- Frequency of mitigation activities. Your risk mitigation plan should determine the frequency with which mitigation activities must be carried out in order to keep the plan relevant to new threats and risks your organization can experience. Make sure to specify in your plan when and which mitigation steps to repeat as well as which strategies and controls to review.

Since describing the steps of the insider risk mitigation process is the key aspect of this plan, we need to take a closer look at this point.
Remote Employees: How to Manage Insider Risks
4 main steps to mitigating insider risks
Before planning mitigation activities, make sure your organization conducts an insider threat risk assessment. The results of this assessment will help you identify:
- possible risks, their impact, and their likelihood
- insider threats your organization may experience
- vulnerabilities that may be exploited by malicious actors
- sensitive resources that may be endangered by malicious insider activities
Once you’ve discovered and assessed possible insider threats and risks, you can start planning mitigation activities.
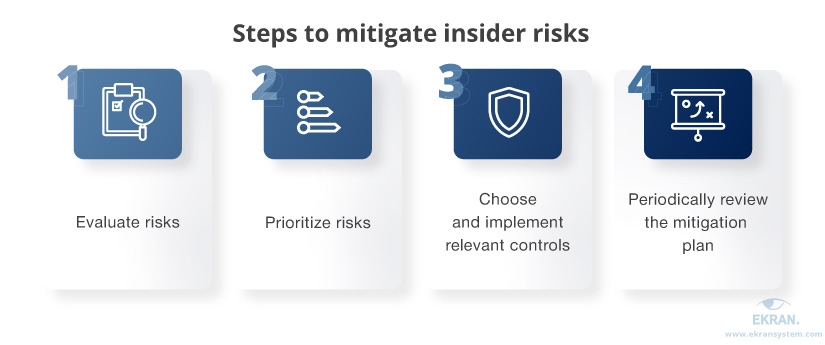
The results of the risk assessment are the basis for risk mitigation activities. The first of these activities is an insider risk evaluation, which assesses the severity of a risk based on its probability and possible impact.
There are different ways to evaluate insider risks. The most common is to create a probability/impact matrix. In this matrix, the horizontal axis shows an estimate of the impact of a risk on your organization from trivial to extreme. The vertical axis represents the probability of a risk’s being realized, from rare to very likely.
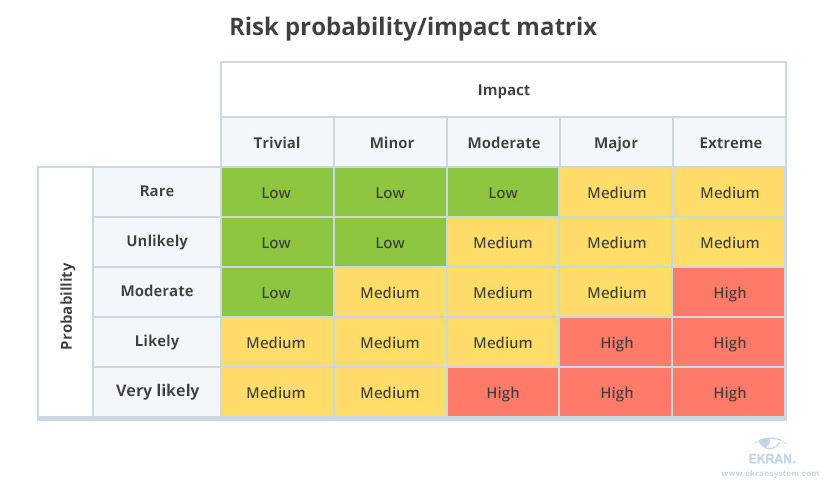
With risk evaluation results at hand, you can proceed to the next mitigation step — insider risk prioritization. Prioritizing risks helps you to:
- determine which risk you need to address first
- choose a mitigation strategy for each risk
- select the most effective risk reduction controls for each risk
You can prioritize insider risks manually by analyzing their probability and severity, the history of insider incidents in your organization, and the specifics of your industry. Or you can use ready-to-go solutions that will prioritize risks for you.
The last step of the mitigation process is choosing and implementing relevant controls that help to eliminate or reduce insider risks. These controls can be:
- new threat mitigation techniques, policies, and tools
- insider threat awareness training for employees
- improvements to data protection
After you choose and implement controls that mitigate insider risks in your organization, remember that risk mitigation planning is never really over. After a certain period of time, you need to review your risk mitigation plan and controls. New insider risks and threats will appear as your organization grows and changes. That’s why you should periodically adapt your risk mitigation strategies to the present reality.
In the next section, we take a look at the most common security measures and solutions that can be part of the mitigation process.
How Can MITRE ATT&CK Help You Mitigate Cyber Attacks?
Which activities help mitigate insider risks?
The set of activities and tools you should use to mitigate insider risks highly depends on the mitigation strategies you choose. However, there are some common security measures and solutions that can fit most mitigation scenarios. Let’s take a look at these controls and how you can implement them with Syteca.

1. Create a cybersecurity-oriented corporate culture
Negligent employees and contractors are the key sources of insider threats. According to the Ponemon Institute’s 2020 Cost of Insider Threats Report [PDF], negligent employees and contractors were responsible for 63% of insider attacks in 2019.
Employees and contractors usually make mistakes because of lack of attention, poor knowledge of cybersecurity policies, or a desire to save time by breaking security rules. You can reduce these risks by creating a cybersecurity-oriented corporate culture.
Here are the key steps towards building such a culture:
- Educate employees about common security threats
- Show employees possible consequences of outsider and insider attacks
- Make sure employees clearly understand the consequences of neglecting cybersecurity rules
Employees with a high level of insider risk awareness will be more accepting of new security tools and practices and can even help you improve your security system. As a result, you’ll reduce insider risks for the organization by making your employees part of your cybersecurity shield.
People-centric Security for Remote Workers
2. Engage the HR department to detect insider threats
Malicious actions can have both behavioral and technical indicators. You can detect and monitor suspicious behavior inside your infrastructure with cybersecurity tools. But you also need help from the HR department to spot risky behavior outside the digital environment: cases of harassment, regular violations of corporate policies and culture, unusual interest in projects that an employee isn’t involved in, etc.
There are several ways for the HR department to assist you in detecting and preventing malicious insider activity:
- Conduct extensive background screenings when hiring new employees
- Report cases of harassment and risky behavior to security officers
- Communicate with employees to determine reasons for risky behavior and help them change it
- Notify security officers of employee status changes like promotions and terminations to enable officers to modify user access rights
3. Limit access to sensitive resources
Managing user access is one of the cornerstones of insider risk mitigation. The more access rights users have, the more harm they can inflict if they decide to go rogue, so you want to limit users’ access to sensitive resources as much as possible. However, employees should be able to interact with all the resources they need in their work routine.
A way to solve this challenge is by creating a granular role-based access control system, where a user’s access rights depend on the user’s role in your organization. With a role-based control system, employees should be able to access only the resources they need for work. This way, cybersecurity measures will limit the possible attack surface without disrupting employees’ workflows.
With Syteca, you can easily set up and manage role-based access. Our platform can help you:
- granularly configure and change access rights for each user and user role
- manually approve or deny access to sensitive resources
- provide time-based access to critical assets
- securely manage user credentials
4. Monitor user activity
User activity monitoring (UAM) is needed to keep an eye on the sources of insider risks — users in your system. Today’s monitoring tools allow you to watch user sessions online to assess suspicious activity or review records later to analyze security incidents and determine damage caused by them.
Syteca UAM software records a lot of metadata on user activity, including keystrokes, opened files and folders, URLs, and executed commands. Additionally, Syteca can enable you to monitor and manage USB devices. Continuous activity monitoring and recording is the first step to ensuring a fast and efficient incident response. Also, recordings help you analyze past security incidents, which can be useful for improving mitigation activities.
5. Speed up cybersecurity incident response
It’s essential to respond to cybersecurity incidents as fast as possible. The more time malicious actors have, the more damage they can inflict.
Responding quickly is also quite a challenging task, since insiders know their way around your cybersecurity system and can cover their tracks. That’s why the average time to detect and remediate an insider attack is 77 days according to the Ponemon Institute report mentioned above.
To be able to respond to a threat fast, you need to stay alert to potential security incidents. Deploying a dedicated software solution and using a MITRE ATT&CK model for mitigation can help. When monitoring user activity with Syteca, your security team will receive instant alerts each time our solution detects suspicious actions or cybersecurity rule violations.
When you receive an alert, you can review the associated user session online and block it if needed, preventing an insider attack from going further. Also, you can configure Syteca to automatically respond to detected incidents.
Real-time User Activity Alerts and Incident Response
6. Leverage artificial intelligence (AI) to detect insider threats
Detecting early indicators of insider activity helps mitigate risks even before a malicious or negligent actor starts harming your organization.
User and entity behavior analytics (UEBA) solutions are designed specifically to detect abnormal and possibly harmful activities. They leverage the power of AI and machine learning algorithms to:
- analyze user activity monitoring data
- create a baseline of normal user behavior
- detect behavioral anomalies and alert security officers
A UEBA solution can help you detect suspicious actions that no other cybersecurity tool will report. For example, Syteca’s UEBA analyzes employees’ working hours and alerts security officers when an employee starts working at an unusual time, as this is a possible indicator of an insider threat.
7 Best Practices for Building a Baseline of User Behavior in Organizations
Conclusion
Insider threat mitigation in cybersecurity is one of the essential activities that allows your organization to prevent insider-related security incidents or reduce the damage they cause.
In this article, we showed you how to plan an insider risk mitigation process and which common security controls you can implement. It’s possible to deploy most of them with just one piece of insider threat detection software — Syteca. Our insider risk management platform empowers you to detect, deter, and disrupt insider threats at early stages.
Request a free trial to see how Syteca can help you mitigate insider risks!





