In striving to make sure in-office and remote employees’ work is secure, organizations often rely on technology-centric approaches. Although user monitoring tools and other cybersecurity solutions do their jobs, they still can’t affect employee behavior and fully secure remote work. To engage remote employees into cybersecurity, organizations are now shifting to a human-centric approach.
The people-centric approach to security aims to treat workers more as a cyber shield for corporate data rather than a vulnerability. In this article, we explore what this approach is, why you may want to implement it, and how your organization can benefit from it.
What is people-centric security?
Human-centric security is about making your people your defense.
Attackers target people, not machines. That’s why organizations are gradually shifting from a technology-centric to a human-centric cybersecurity approach.
Traditional cybersecurity software protects data by monitoring user activity, restricting employees’ access to certain resources, and blocking phishing emails. However, such software can’t fully protect an organization from security events caused by human errors.
So instead of emphasizing restrictive security controls, businesses are putting more effort into:
- Providing relevant cybersecurity education for employees
- Emphasizing employees’ accountability for their actions
- Showing workers that an organization trusts them
This is where people-centric security comes into play.

Definition of people-centric security by Gartner
People-centric security is an approach that treats people as an important security perimeter. Its main principle is enabling each employee to have autonomy in handling information, using devices, and adopting security measures.
When discussing people-centric security (PCS), cybersecurity specialists often refer to this approach using the following terms:
- People-centric security approach
- People-centric security framework
- People-centric security strategy
- Human-centric security
- You-shaped security
In this article, we use these terms as synonyms.
While promoting trust in employees and making them responsible for the security of corporate data they work with, PCS doesn’t cancel the need to verify that employees follow recommended cybersecurity practices.
Just like in a conventional technology-centric approach to security, in PCS, users still have a particular set of access rights depending on their position, work routine, and responsibilities. However, within the PCS framework, employees are more aware of possible vulnerabilities, cybersecurity incidents, and their consequences. Also, employees are ready to take responsibility for their actions.
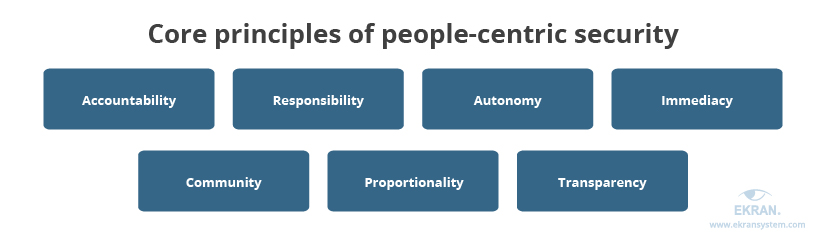
There are seven principles that should govern the increased rights and responsibilities of employees under a people-centric security framework:
- Accountability — Owners of information must be accountable for protecting it.
- Responsibility — Employees must take responsibility for how they handle data, use devices, etc.
- Autonomy — Organizations should provide workers with trust and enable self-governance.
- Immediacy — Inappropriate behavior always should be followed by an adequate response: punitive actions, educational program enhancements, etc.
- Community — All employees within an organization should maintain and support a positive cybersecurity culture.
- Proportionality — Control measures have to be proportional to the risks: the higher the risks, the stronger the controls.
- Transparency — Organizations should verify employees’ attitudes with user monitoring solutions and provide feedback on what to improve to reduce cybersecurity risks.
Within a modern cybersecurity program, human-centric security should go hand in hand with traditional perimeter and access control security. Only by combining the PCS approach with robust user cybersecurity software can organizations enhance their data and system security.
Why do you need human-centric security?
Security that doesn’t work for people doesn’t work.
Implementing PCS into your work environment means making employees a cybersecurity shield for your organization. But is it really worth the effort?
Let’s define the three ways you can benefit from deploying a people-centric approach to cybersecurity:

1. Create a secure perimeter that isn’t covered by cybersecurity software
Hackers continually find new ways to manipulate both humans and systems. Because of this, organizations need to revise cybersecurity measures and update their tools each time they learn of a new threat. However, this doesn’t always provide employees with enough awareness and can’t protect organizations from social engineering attacks.
For example, phishing campaigns may be so advanced they can easily bypass email filters and cybersecurity tools. Thus, it’s up to users to be extremely attentive with emails they receive.
It’s essential to understand that well-trained staff is an important part of any cybersecurity defense. When properly educated and nurtured in a healthy cybersecurity environment, employees can:
- Use an organization’s networks and devices responsibly
- Carefully handle the data they work with
- Wisely access internet resources
- Know how to securely share data through cloud-based solutions
- Successfully identify phishing emails
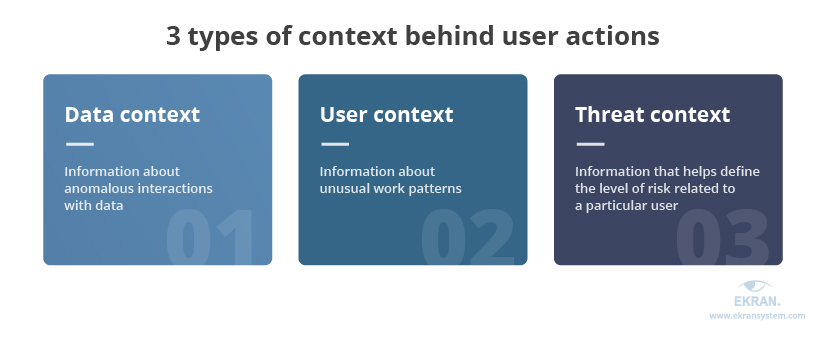
2. Understand the context behind user actions
Although user activity logs provided by employee desktop monitoring software often help cybersecurity officers detect suspicious activity, they can’t help officers understand people. And to truly understand people, you need to know their intentions — what’s behind their actions.
Knowing the context behind user actions is important, especially when tasks may require creative solutions. In such situations, unusual employee activity — launching new applications or spending more time interacting with certain data than usual — might seem suspicious but not bring any threats.
Also, context can make it clear whether a user performed an inappropriate action by accident or with malicious intent.
Context can be related to data, user activity, and possible threats. By analyzing it, organizations can faster detect and respond to potential threats as well as make informed decisions on existing cybersecurity measures.
3. Improve the security of remote work
PCS isn’t a new trend, but in 2020, it found a new lease on life. With the need to shift to remote work, businesses switched their cybersecurity focus from machines to humans.
Cybersecurity officers usually consider remote employees a significant risk for corporate data and systems for numerous reasons:
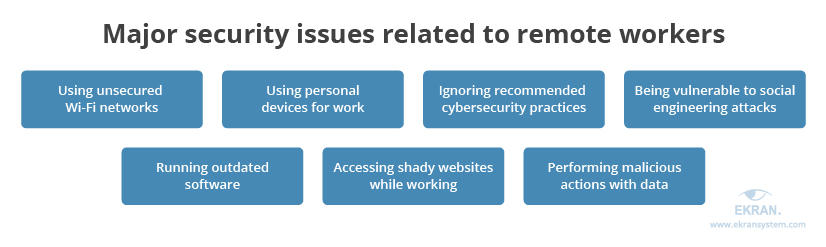
While traditional cybersecurity tools help to handle some of the issues mentioned above, the PCS approach provides remote employees with much more awareness of cybersecurity risks and their consequences. Thus, employees are more likely to follow an organization’s cybersecurity policies even when working from home.
Human-centric security goes far beyond ordinary cybersecurity training. Conventional training gives no guarantee that employees won’t forget or neglect certain practices, especially when they’re overwhelmed with work. Meanwhile, PCS concentrates on employees’ responsibilities and teaches them to be more cautious about potential cybersecurity issues, especially when they’re working remotely.
Remote Employee Monitoring: How to Make Remote Work Effective and Secure
How to implement PCS in your organization?
Be ready to commit.
There’s no one-size-fits-all plan on how to enhance an organization’s cybersecurity with PCS. However, there are three major steps that will help you shift your cybersecurity focus from machines to people.
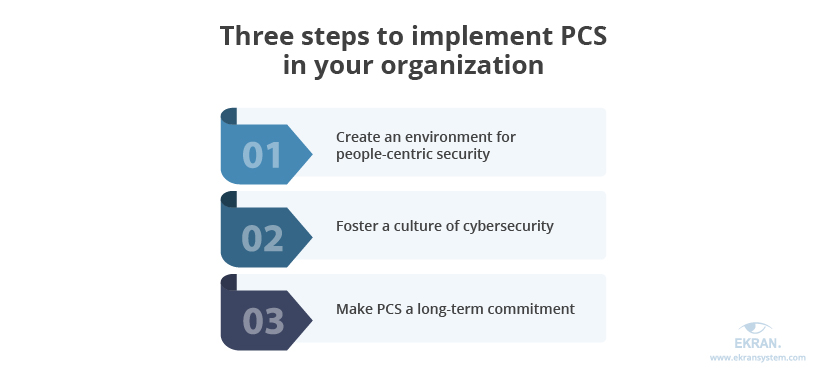
1. Create an environment for people-centric security
One of the key ideas of PCS is to allow employees to make risk-based decisions. To achieve this goal, you need much more than traditional security awareness and training.
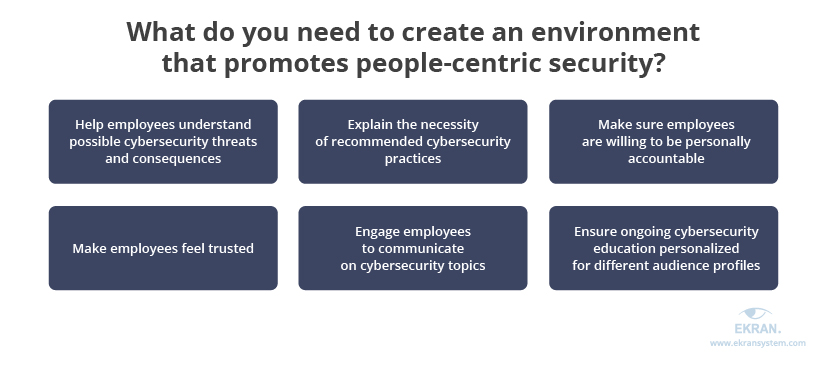
Concentrate on creating a work environment for people-centric security, in which employees:
- Comprehend cybersecurity threats and their consequences
- Understand the necessity of following recommended cybersecurity practices
- Are willing to take personal accountability for their actions
- Know the company trusts them and provides relevant controls to manage their security
- Communicate freely with executives and security officers on cybersecurity topics
- Have access to corporate educational materials that are tailored to different audience profiles and are regularly updated to address common mistakes, new threats, etc.
2. Foster a culture of cybersecurity
An organization’s security culture can impact the organization in multiple ways, negatively or positively affecting compliance, the number of vulnerabilities, the likelihood of cybersecurity incidents, and the organization’s financial state.
You can evaluate your current security culture by assessing the following seven elements and finding areas for improvement:
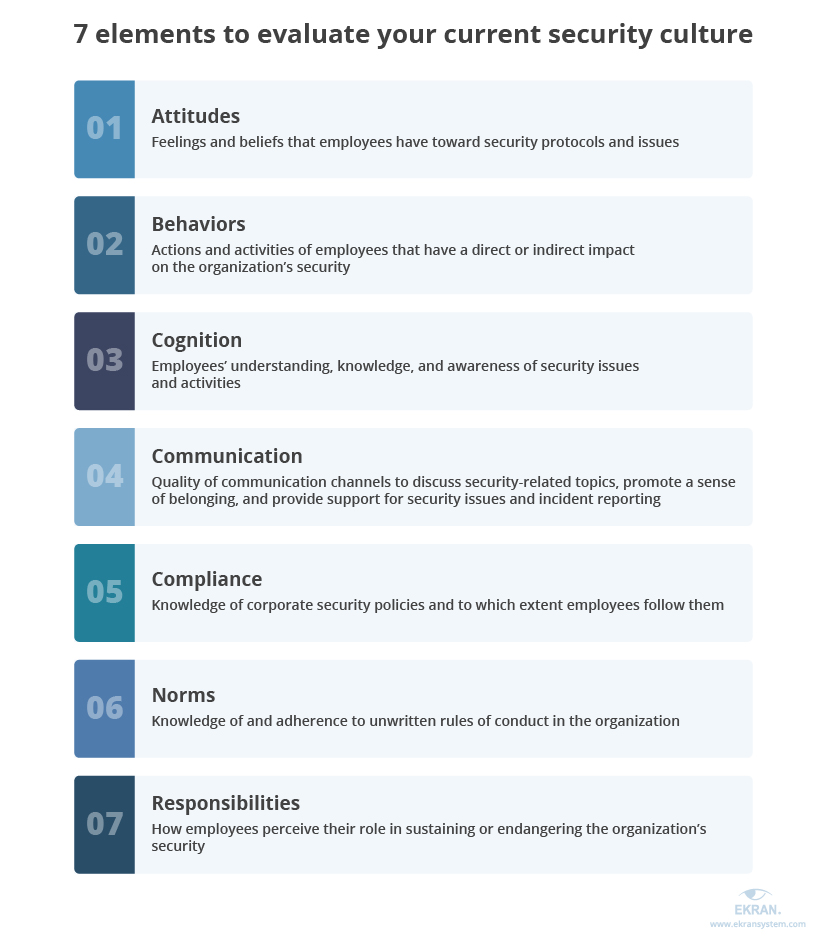
According to the Security Culture Report 2020 by KnowBe4, Inc. [PDF]
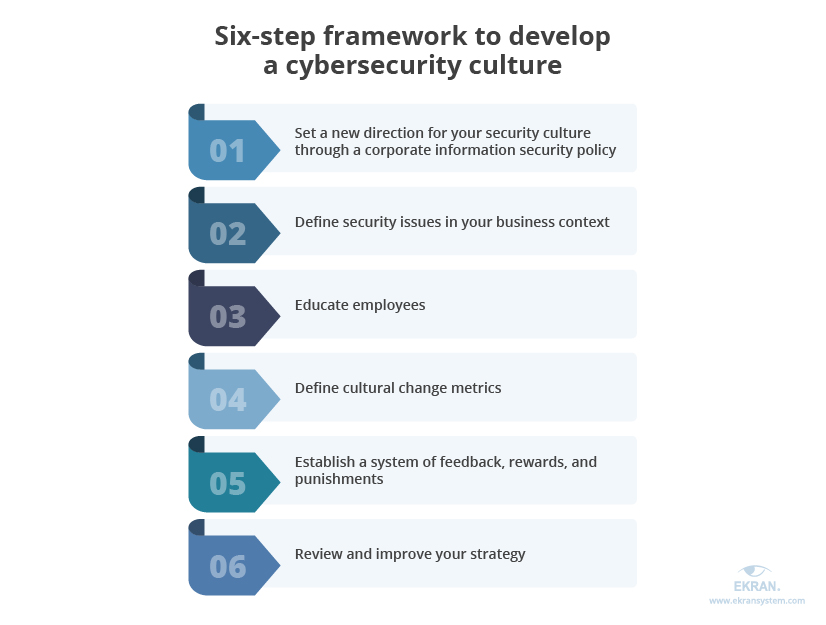
Once you’ve performed this evaluation, you can start working on your cybersecurity culture. There are different approaches to develop it. Let’s take a look at the following six-step framework offered by the European Union Agency for Cybersecurity:
3. Make PCS a long-term commitment
Establishing a healthy cybersecurity culture and an environment for people-centric security is a long process that requires thorough planning, continuous employee education, and regular evaluation of the results. If your organization aims to adopt the PCS approach, you should be ready to commit.
This strategic commitment could take the following forms:
- Choosing a fitting methodology, tools, and evaluation methods on your own
- Hiring a management consultant who specializes in cybersecurity culture and driving business change to help you
The first method may be time-consuming at the beginning, since your cybersecurity officers will have to explore the PCS approach in detail. On the bright side, it will give you a clear picture of all the options available and a deeper understanding of the value of PCS.
Hiring an experienced consultant will definitely save your time and allow you to start implementing the PCS approach much faster. However, it will require additional funds.
4 key elements of securing remote work with a people-centric approach
Let’s explore practices and tools that will help you in establishing a beneficial human-centric security framework within your organization.

1. Customized security training
The major goal behind customized security training is to help employees:
- Understand common risks, threats, and their consequences
- Be prepared for industry-relevant threats
- Always follow cybersecurity practices
- Be able to recognize social engineering attacks and other threats
A great way to achieve this goal is to personalize training and all the cybersecurity materials your employees are asked to get familiar with. By customizing training for the specifics of your organization and the routines of different types of users, you can help employees recognize themselves and better grasp useful information. When information is standardized and bland, employees tend to get bored and lose attention.
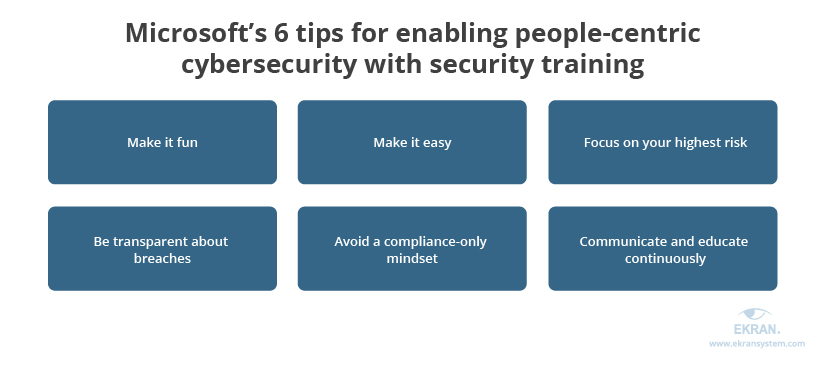
Microsoft has prepared the following six helpful tips to enhance your security training strategy with a people-centric approach:
2. Artificial intelligence (AI) and machine learning (ML) tools
Both AI and ML technologies are already used in cybersecurity software to detect potential threats and mitigate hacker attacks. However, they can also be applied to help employees learn an organization’s security rules and reduce cyber risks related to human factors.
As part of robust user activity monitoring software, AI and ML can:
- Monitor user behavior
- Detect cybersecurity violations and potentially dangerous actions
- Trigger user notifications of security violations
Some cybersecurity solutions allow for configuring notifications that educate users on detected violations. Thus, such technologies can gradually change user behavior towards security and foster a cybersecurity culture within an organization.
3. Simulated social engineering attacks
Organizations often use simulated social engineering attacks to check how well employees have grasped cybersecurity training. These attacks can include phishing, pretexting, and baiting.
For example, you can create phishing emails that are harmless but that help you see how employees will behave during attacks. This allows you to learn why employees act insecurely, and you can use this information to personalize your security training and cover gaps in your human cyber shield.
Although the click rate will give you some indication of organizational vulnerability and an idea of how effective your security training is, you shouldn’t strive to receive the perfect score. Making the click rate the key marker is wrong because anyone can be phished; it just takes the right email, at the right time, in the right situation.
4. Communicating risks
Risk assessment is the basis of any security program. By determining and evaluating risks relevant to your organization, you can effectively adjust your cybersecurity strategy to combat possible threats. However, this helpful information shouldn’t only be used by C-level executives and security officers.
PCS can succeed only when all employees have enough tools and knowledge to be a true cyber defense for an organization. Consider risk assessment reports as material that can be reworked into helpful brochures and slides for the next security training.
When exploring the real facts and numbers, employees begin to treat cybersecurity like a real thing, not a hypothetical danger. Thus, they’re more likely to change their attitudes and behaviors, which will help you build a strong cybersecurity culture within your organization.
Insider Threat Risk Assessment: Definition, Benefits, and Best Practices
How can Syteca assist you with people-centric security?
Syteca is a comprehensive insider risk management platform that helps organizations detect and prevent insider threats. In addition, it allows you to immediately respond to potential incidents and provides detailed context for their further analysis.
In terms of people-centric security, you can use the Syteca platform to:
- Monitor user activity of in-office and remote employees to know who accesses what
- Set warning messages on violations to help users better learn your organization’s cybersecurity rules
- Detect abnormal user activity and mitigate a potential risk before it turns into an incident by leveraging AI-based user behavior analytics
- Analyze essential user activity data with extensive customized reports
Syteca can also help you comply with major cybersecurity regulations, laws, and standards like NIST 800-53, SWIFT CSP, HIPAA, GDPR, FISMA, and PCI DSS.
Privileged Password Policy Compliance Overview: NIST 800-63, HIPAA, PCI DSS, GDPR
Conclusion
Traditionally, we think of cybersecurity as something that’s highly technical: antivirus software, secured networks, complex infrastructure. However, in reality, malicious actors often target people who have access to the data they want. This means we should pay attention to employees’ cybersecurity knowledge and the ability of employees to recognize potential threats.
Shifting to a people-centric security approach means providing employees with more knowledge, tools, awareness, and self-governance. Implementing this approach can help organizations significantly reduce cyber incidents caused by human factors.
Using robust RDS monitoring solutions along with implementing the people-centric security approach is a great combination to enhance your cybersecurity. Syteca will help you prevent insider threats without disturbing the work of remote employees. Request a free trial of Syteca below to see it in action.




