Securing an organization’s sensitive data is hard, especially when the danger comes from within. A careless coworker may insecurely share credentials, an intruder may compromise an account, or a malicious insider may misuse their access rights. According to the 2020 Cost of Insider Threats Report [PDF] by IBM, 60% of organizations experienced more than 20 insider-related incidents in 2019.
One promising solution to prevent insider threats is user and entity behavior analytics (UEBA). Introducing a UEBA mechanism to your cybersecurity program can help you detect malicious activity before it harms your organization. In this article, we explain what UEBA is and how it works. We also offer seven best practices to build a behavioral baseline.
All you need to know about user and entity behavior analytics
What is UEBA?
User and entity behavior analytics is technology for detecting and investigating suspicious activity of a user or entity. The term “entity” usually refers to non-human system users: service robots, daemons, routine automation tools, etc.
UEBA solutions profile and detect anomalies in user and entity behavior using a combination of basic and advanced analytical methods like machine learning. They can be integrated into comprehensive cybersecurity solutions or be standalone tools.

Definition of user and entity behavior analytics by Gartner
When working, employees leave digital footprints all around the corporate system: they access certain files at certain times, start and finish their work according to a routine, visit more or less the same websites every day, etc. Significant deviations in their behavior may be a sign of malicious activity or a compromised account.
During the baselining period, a UEBA system observes user behavior to establish baseline behavior. During further monitoring of user and entity activities, the UEBA system detects deviations from baseline behavior and sends alerts of suspicious activity and potential insider threats.
5 Levels of User Behavior Monitoring
Why do organizations need UEBA?
Behavior analytics may help security officers spot potentially risky user activity before an incident happens. Let’s take a look at the key benefits of UEBA in detail:
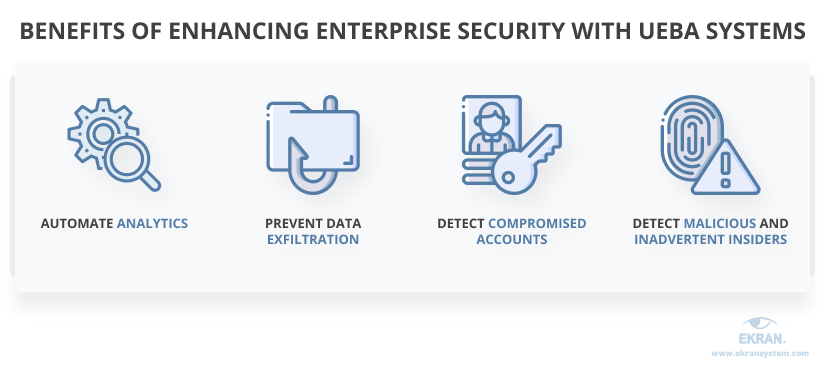
Automate analytics. Thanks to artificial intelligence (AI) algorithms, UEBA systems can analyze millions of user actions in a matter of seconds, which is simply impossible for security officers. This significantly increases the chances of detecting dangerous activities and minimizes the data that security officers need to process.
Prevent data exfiltration.UEBA systems can detect abnormal user activity such as suddenly downloading massive amounts of data or accessing corporate networks from a new location that can potentially lead to data leaks or exposure. Also, UEBA helps security officers react to potential threats immediately. Once they’re notified, officers can check whether threats are real. This is why UEBA is a significant part of cybersecurity strategies that aim to prevent data exfiltration.
Detect compromised accounts. When a hacker penetrates a corporate system using stolen credentials, they will definitely behave differently than your employees. An intruder is more likely to search for and copy sensitive information rather than open a document on which your accountant has been working for the last two weeks. This is where a UEBA module should notice abnormal behavior and alert security officers.
Detect malicious and inadvertent insiders. These types of security threats are difficult to detect. Insiders spend most of their work time performing their routines and might act maliciously only for short periods of time. However, if these short periods of malicious activity significantly deviate from an employee’s usual routine work, a strong UEBA solution will notice.
Inadvertent insiders usually cause data breaches by one-off actions like sharing passwords, accessing corporate systems from unsecured Wi-Fi connections, or opening a phishing email. Сomprehensive monitoring solutions with integrated UEBA modules can be configured to react to such security violations.
However, the efficiency of detection will depend on the number of behavioral factors that the system monitors, correlates, and analyzes, as well as on how well the machine learning algorithms were tuned during baselining.
What Is an Insider Threat? Definition, Types, and Countermeasures
How does UEBA work?
To understand user and entity behavior analytics, let’s look closer at how UEBA tools work. While vendors can add different features and keep secret their methods for anomaly detection, the main steps that each UEBA system takes are basically the same.
A common UEBA solutions works in the following way:
- Monitors user and entity activities and collects data about them from system logs
- Applies advanced analytical methods to analyze collected data
- Creates a baseline of user behavior by finding behavioral patterns and activity intervals and establishing thresholds and deviations within which behavior is considered acceptable or normal
- Builds a baseline of users’ behavioral patterns, then compares them to the behavior of employees with similar duties (peer groups) to fine-tune in order to detect possible deviations
- Compares current user behavior with the established baseline and decides whether deviations are acceptable or anomalous
- In case an anomaly is detected, the system estimates the degree of deviation and its risk level and sends alerts to security officers in real time
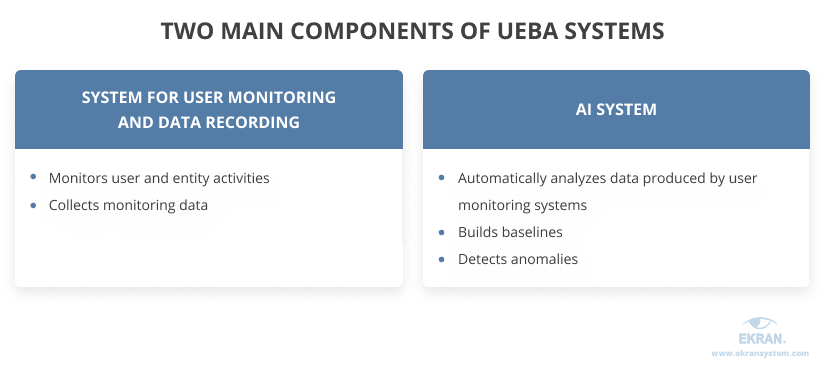
The functioning of UEBA systems is based on two main components: a system for user activity monitoring and data recording (such as Windows, Linux, Citrix monitoring software) and an AI system. Data is collected on various behavioral factors, from websites visited to typically used applications and typing rhythms.
UEBA systems don’t consider all anomalies as risky, since employees may change behavior due to reasons like optimizing routine processes or getting new responsibilities. Also, there may be periods of unusual activity when people need to finalize annual reports or check on arrangements before going on vacation, for example.
Instead, UEBA solutions evaluate the possible impact of a certain anomaly. They alert security officers of high-risk events like suspicious access to sensitive information. Then, security officers check whether a potential threat is dangerous and can tune the UEBA tool’s settings in case of a high rate of false positives.

Real-time User Activity Alerts and Incident Response
7 best practices for building a baseline of user behavior
Let’s explore the seven best practices for user behavior analytics that explain what to keep in mind when building a baseline for user behavior.
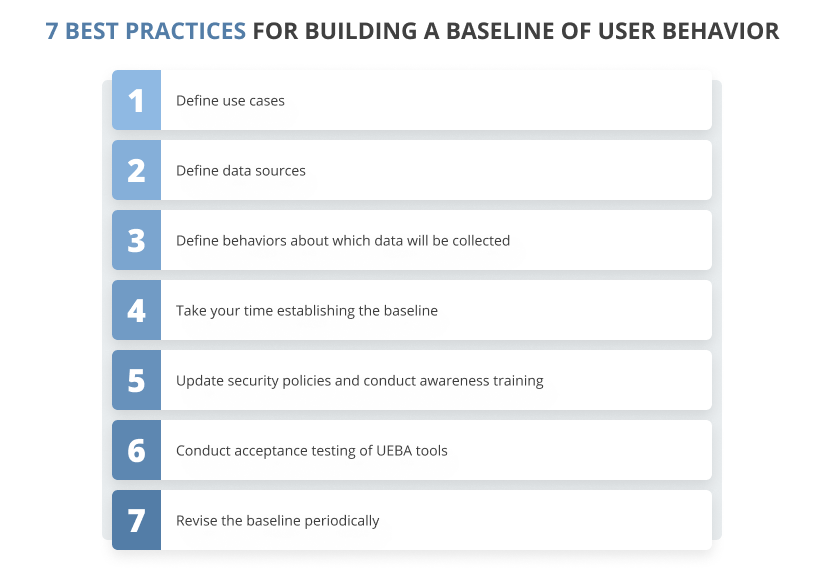
1. Define use cases
Before choosing a UEBA solution, define the use cases you want to address. These can be identification of malicious insiders, compromised users, or known security threats.
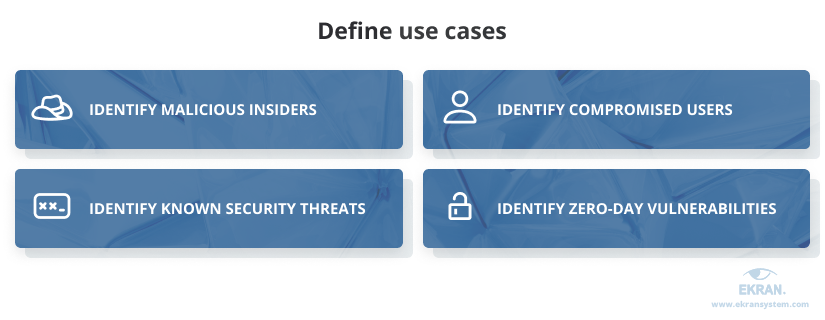
Knowing what risks you need to identify in the first place and what output you expect from your UEBA tool will give you a hint about what data you need to collect for behavior monitoring.
2. Define data sources
The next step is to make sure the UEBA solution you’re choosing can support your use cases and can collect all the necessary data. Depending on your goals, this data may include events and logs, business context data, and HR information like performance history.
When choosing a UEBA solution, pay attention to those that can work with different types of data. The more data types a tool can handle, the more precise the baselining will be. Also, you may discover the need to enrich information about user activity with more data in the future. This could include network and endpoint data or non-structured behavioral data such as emails, HR records, or social media activity.
Also, consider implementing a comprehensive cybersecurity solution that already has a UEBA module instead of a standalone tool. For example, consider a user monitoring software that can gather and analyze various types of data and use AI-driven technologies for behavior analytics.
3. Define behaviors about which data will be collected
The effectiveness of UEBA tools highly depends on the variety and amount of data it collects for analysis. UEBA tools can gather and analyze information upon various factors, such as working hours, applications used, and typing rhythms.
When you know what types of data a UEBA system collects, you can better define the effective period for baselining and understand possible reasons for false positives. Here’s a list of some behavioral factors about which a UEBA system can gather data for baselining:
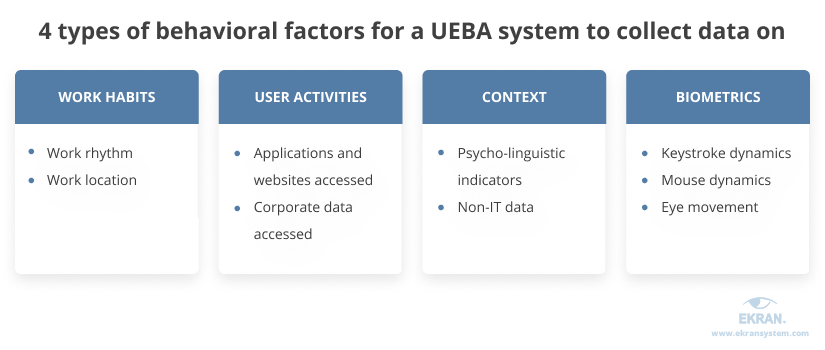
Let’s explore these factors in detail.
Work habits
Work rhythm. Employees usually behave similarly from one day to the next during their working hours. You may spot some deviations in an employee’s routine close to the end of an accounting period or if an employee moves to another department or gets promoted. However, you should keep an eye on anomalies like accessing the corporate network in the middle of the night, since it might be a sign of malicious activity.
Work location. Spotting suspicious working locations is more complicated nowadays, since employees may access corporate servers from the office, home, networking spaces, and even other countries. However, it’s still unusual when someone tries to authenticate from two different places at the same time or from a host they’ve never used before.
User activities
Applications and websites accessed. Most employees use the same range of applications during the same time periods each day. If someone downloads a new application or visits a prohibited website, it may be a sign of a compromised account or a phishing attack.
Corporate data accessed. Since access to corporate data is a potential source of risk, organizations tend to limit access according to people’s work duties. However, in many real-life scenarios, the zero trust approach might not always work, leaving users with access to a wide scope of data. A UEBA system can detect anomalies here – for instance, it might look suspicious if a marketing specialist opens a database with clients’ financial information.
Why Do You Need a Just-in-Time PAM Approach?
Contextual factors
Psycholinguistic indicators. Studies show that the language people use can indicate possible insider threats. Some UEBA systems can also analyze user activity monitoring and keystroke monitoring data to detect changes in email activity and language used by employees. Thus, they can determine changes in employees’ sentiment that may point to possible security risks.
Non-IT data. In addition to technical data, UEBA tools can collect data from human resources and other business applications. This data provides the UEBA tool with information about vacation periods, job duties, and projects on which employees work.
Biometric factors
Keystroke dynamics can be used to define behavioral profiles for the way people type. Each of us has our own typing speed as well as the tendency to make typical mistakes in certain words. If a UEBA solution detects severe deviations in keystroke dynamics, it may alert about a compromised account.
Mouse dynamics take into account a user’s interactions with the mouse. Mouse dynamics for user authentication are based on the time duration between clicks as well as the unique speed, rhythm, and style of cursor movement.
Eye movement biometrics are based on distinctive eye movement patterns and can be used for preventing insider attacks. People move their eyes in unique ways, and these patterns may be used to distinguish people. Eye and gaze tracking tools can record videos of eye movements. This type of behavior biometrics can detect cases when an authorized user is out of the workplace and a co-worker tries to compromise their workstation.
Incident Response Planning Guideline for 2021
4. Take your time establishing the baseline
UEBA vendors usually recommend a duration for the baselining period, but you should also take into account the specifics of your business. For instance, pay attention to the time of year when you establish your baseline, since a peak period of employee activity is not the best time for it.
The time for baselining can vary from one week to 30 or 90 days depending on the specifics of user activity. During this time, a solution’s machine learning engine will learn an organization’s data and construct baselines. Also, this baselining period will allow you to validate the UEBA solution and its outputs.
Spending less than a week on monitoring work activities may result in a high rate of false positives. However, if you establish a baseline for too long, the system may mark some malicious events as normal.
5. Update security policies and conduct awareness training
Make sure to inform employees about the deployment of UEBA tools from the very beginning, telling how the technology will be used and conducting awareness training.
Another thing to keep in mind is that UEBA technology can’t replace investments in security awareness training and management. During the adoption period, a high rate of false positives may negatively affect employee morale.
To avoid this, security officers should comply with predetermined escalation procedures that include the participation of HR, legal counsellors, and team leads when they investigate potential attacks. Analyze alerts with extraordinary care so that dedicated employees don’t begin to think they’re no longer trusted.
Additionally, use other security solutions such as user recording software in order to double-check for incidents or security violations that may occur during the baselining period.
PECB Inc. Deploys Syteca to Manage Insider Threats [PDF]
6. Conduct acceptance testing of UEBA tools
Once the baseline is established, you need to conduct acceptance testing of your UEBA tool to see how it works and whether it needs any improvements.
First, define use cases you want to test. Then, run the system for testing purposes and analyze its output. Review your findings and analyze the rate of false positives. If the rate of false positives is too high, you may need to enrich information about user activity with additional monitoring data by continuing the baselining period.

7. Rebuild the baseline periodically
User and entity activities are constantly changing. Employees can change their tasks and projects, for instance, so their behavior will obviously vary from time to time.
Most UEBA systems automatically collect data and adjust the baseline periodically thanks to their machine learning algorithms. However, when your enterprise faces major structural or personnel changes, you may need to establish a new baseline for continued effective operation of the UEBA system.
How the Syteca UEBA module helps you enhance data security
As an insider risk management platform, Syteca includes multiple functionalities that work together to help you establish comprehensive user monitoring and insider threat detection and prevention.
One of its key features is user and entity behavior analytics functionality. Powered by artificial intelligence algorithms, the Syteca UEBA module builds a baseline of user behavior and detects anomalies in the routines of internal users. For instance, it will notify your security officers in case an employee accesses the corporate network during non-working hours.

Leverage the opportunities of the Syteca platform to detect threats and respond to them in real time:
- User and entity behavior analytics — Detect abnormal user activity and possible account compromise.
- Predefined and custom alerts — Explore a collection of alert templates that cover the most common insider threats and easily configure your own rules.
- Automated incident response — Set up automatic response actions like warning messages or user blocking for potentially suspicious activities.
AI-powered User Behavior Analytics [PDF]
Conclusion
Mitigating insider risks is challenging. One of the most promising approaches for doing so is establishing a user behavior baseline and detecting abnormal activity.
By introducing UEBA tools to your cybersecurity strategy, you significantly increase the chance of detecting user-related threats and preventing data breaches.
Make sure to:
- Determine the major use cases you want to cover with user behavior analytics
- Determine data sources to collect information on your users
- Establish a reasonable time period for baselining
Syteca offers a comprehensive insider risk management solution that collects a wide range of information regarding user activity including keystrokes, launched applications, and opened web pages. Its AI-powered UEBA module can create detailed and accurate baseline profiles for effective detection and response to insider threats.

Request a trial version of Syteca to enhance your cybersecurity now!




