Insider incidents, whether intentional or unintentional, can harm your organization in the form of financial and reputational losses, compliance violations and fines, and operational disruptions. What can you do to avoid this? How can you protect yourself against insider threats? The solution is simple: fortify your organization’s security processes with a carefully executed insider threat strategy.
In this comprehensive guide, we go through insider threat protection best practices to safeguard your organization’s security and minimize insider threats. Don’t wait until it’s too late — start implementing these practices today to protect your business from within.
What are insider threats?
As the term suggests, insider threats are cybersecurity risks that come from people within a company. These people may be employees, contractors, partners, or anyone else who has access to your sensitive information or systems and can accidentally or intentionally cause serious damage to your organization.
Inside actors are typically divided into malicious insiders, careless insiders, and compromised insiders.
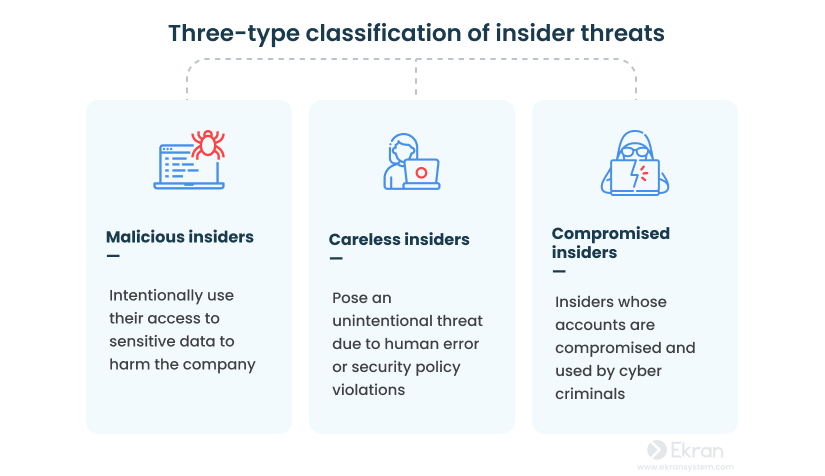
No matter their type, numerous internal data breach examples show that inside actors can cause significant harm to an organization’s data, reputation, and financial well-being. Insider threats can lead to:
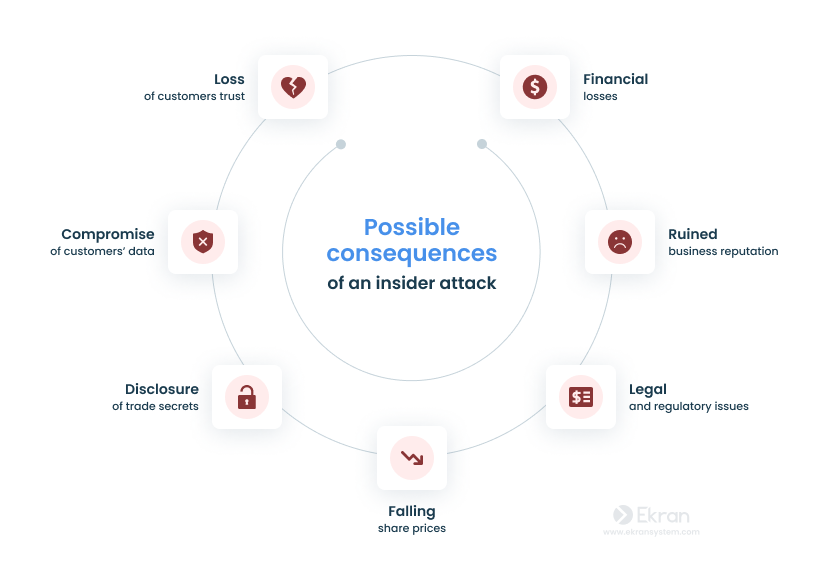
- Disclosure of trade secrets
- Legal and regulatory issues
- Compromise of customers’ data
- Financial losses
- Falling share prices
- Ruined business reputation and loss of customer trust
The frequency and cost of insider attacks are both high. In 2022 alone, more than half of organizations in the world experienced an insider threat, with average financial losses totaling about $15.4 million. It’s no wonder insider threats have become one of the main concerns for a vast majority of companies.
How can you protect data from insider threats? Detecting and preventing insider threats requires a comprehensive approach combining many cybersecurity measures. Below, we list the ten best practices on how to protect critical infrastructure from insider threats.
Insider Threat Statistics for 2023: Reports, Facts, Actors, and Costs
10 best cybersecurity practices for protecting your organization against insider threats
Implementing the following measures can help organizations prevent, detect, and respond to insider threats:

1. Develop a comprehensive insider threat program
Having a good insider threat program is half the battle won.
A corporate insider threat program is the cornerstone of a cybersecurity strategy. It can help you secure enterprise database, detect potential threats early, and mitigate them before they escalate into security incidents.
Taking the following steps can help you create an effective data protection system for insider threat management:

How to Build an Insider Threat Program [10-step Checklist]
A successful insider threat program can save you many resources by improving your chances of detecting and promptly responding to insider incidents and minimizing the damage they cause. Additionally, an insider threat program can help organizations ensure compliance with IT requirements, which is especially important if your enterprise operates in the financial, healthcare, or government sector.
2. Establish robust cybersecurity procedures to securely onboard and offboard staff members
Safeguard your data with the right onboarding and offboarding processes.
You should take particular cybersecurity steps as part of employee onboarding and offboarding. Security specialists need to define the job responsibilities of new employees and give them permissions accordingly. Stick to a zero trust approach: don’t trust anyone or anything, whether inside or outside the network.
Simply put, security officers must verify and authenticate users and their devices before granting access to the organization’s network. The zero trust approach also involves continuous monitoring and logging of all user behavior to make it easier to detect and respond to potential threats before they cause damage to your company.

When an employee is terminated, the security department should immediately disable the employee’s access to any company accounts and systems, including email, messaging, cloud storage, and other services. Revoking access permissions of departing privileged users is especially vital.
3. Implement strong identity management practices
Identity management is not just about securing access; it’s also about enabling access.
Next comes the question: How can you make sure that the right individuals have access to the right resources, applications, and information within your company? That’s where identity management comes into play. From authorizing users to granting privileged access, identity management covers all procedures for managing user identities, access rights, and authentication mechanisms.
If you want to provide your organization with an additional layer of security, consider using multi-factor authentication (MFA), which can drastically reduce the risk of unauthorized access.
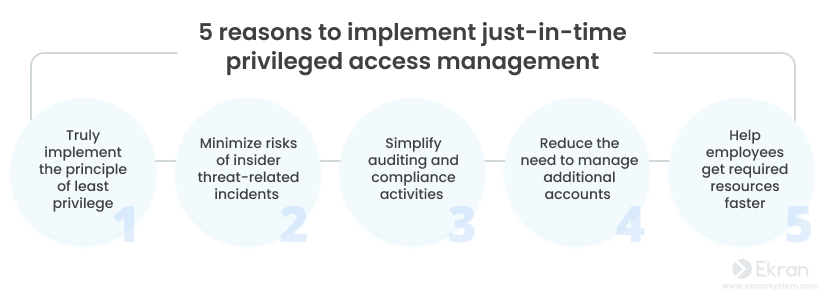
Implementing a just-in-time privileged access management (PAM) approach can help you enhance your company’s cybersecurity strategy further. This approach enables you to provide privileged access to systems and resources for a limited amount of time and only to individuals with valid reasons for having such access. Here are the most common reasons for implementing just-in-time PAM in your organization:
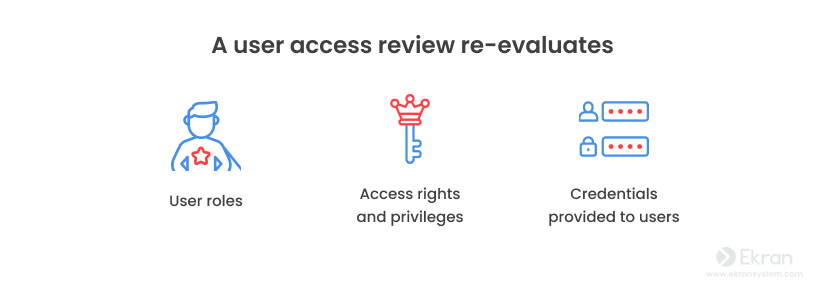
Based on the advice of security guru Bruce Schneier, who says that “security is a process, not a product,” it’s also essential to constantly conduct user access reviews to identify mismatches, reduce potential risks, and ensure that only those users have access to sensitive information who really need it to perform their duties. More precisely, a user access review can help you re-evaluate the following:
6 Best Practices to Conduct a User Access Review
4. Constantly monitor user activity with dedicated software
Trust, but verify.
Monitoring user activity can help you track the way employees process sensitive data and, thus, minimize insider risks. The main activities that security officers should monitor are:
- Unauthorized access to sensitive data or critical systems
- Unusual data transfers to external devices, shared network storage, or cloud services
- Accessing of sensitive data outside business hours
- Unauthorized software installations
- Unexpected changes to user privileges
- Attempts to bypass security measures
- Unusual login activity
- And so on
For effective monitoring of all suspicious processes, the security department should:
- Define threat indicators. By defining threat indicators for the aforementioned activities, security specialists will be able to create alerts and automate response actions.
- Ensure enhanced control of privileged users such as system administrators and other users with elevated access by thoroughly monitoring their activities, access to sensitive data, and changes made to system configurations or settings.
- Regularly review logs to identify any suspicious activity.
- Respond. Once unusual activity is detected, security specialists must analyze logs and alerts as well as take appropriate actions to mitigate potential security risks.
5. Take unusual employee behavior seriously
Abnormal behavior can be a red flag for potential security incidents.
Unusual employee behavior can often be an indication of an insider threat, so it’s important to take such behavior seriously. Companies can benefit from user and entity behavior analytics (UEBA), which employs machine learning algorithms to detect patterns and anomalies in user behavior.
Using a behavior baseline, UEBA algorithms can analyze suspicious information in real time (changes in login patterns, unusual file access, excessive data downloads, etc.) to detect potential threats that may require further investigation. UEBA can identify threats at the earliest stage, allowing security teams to take immediate measures to prevent security incidents. It’s fair to say that UEBA lets you take more proactive steps compared to a traditional rule-based alert system.
5 Levels of User Behavior Monitoring
6. Keep an eye on subcontractors to manage third-party risks
Trust is fine, but control is better.
Third-party vendors and partners can pose significant risks to your organization’s security, as they often have access to databases and critical systems. During 2022, 19% of data breaches occurred because of the compromise of a third-party business partner.
To ensure safe cooperation, perform a security risk assessment before partnering with a third party. Evaluate the cybersecurity policies and data protection practices of potential partners, and find out if they have faced any security incidents in the past. Also, ensure that they meet your security standards and don’t mind you monitoring their activity.
Trust is fine, but control is better. Constant third-party security risk management should become part of your organization’s security strategy.
Third-Party Vendor Security Monitoring
7. Perform regular cybersecurity awareness training
Educating employees is the key to staying ahead of potential risks.
Did you know that 75% of security incidents stem from a lack of cybersecurity awareness among employees? That’s why it’s crucial to perform regular employee training to make sure employees know and follow your organization’s security policies.
Constantly emphasize the importance of following security procedures and the impact of insider threats on your organization and customers. Beware that most users need only a general understanding of insider threats and risks, whereas system administrators, security officers, and privileged users require in-depth knowledge.

Regular cybersecurity awareness training helps you ensure that your employees know what measures to follow to maintain the organization’s security. This will reduce the risk of an inadvertent insider security incident.
Insider Threat Awareness: What Is It, Why Does It Matter, and How Can You Improve It?
8. Constantly perform IT compliance audits
It’s all about compliance.
If you want to make sure that all your cybersecurity practices work as needed, regularly conduct compliance audits. The results of such audits can help you evaluate whether your organization meets the requirements of security regulations, laws, and standards.

To pass a compliance audit, you should conduct a risk assessment, implement strong security controls (and monitor them regularly), and maintain documentation of all your security policies and procedures. Luckily, with dedicated insider threat protection software, your cybersecurity program can become much stronger.
How to Pass an IT Compliance Audit
9. Create a thorough incident response plan
Know how to respond to incidents quickly and effectively.
Unfortunately, only 26% of organizations have a cybersecurity incident response plan according to the Cyber Resilient Organization Study 2021. However, having an incident response plan (IRP) can help you effectively and timely respond to any security incidents that may occur.
A thorough IRP should include certain steps to identify the insider threat and immediate actions to prevent further damage (such as limiting data exposure by isolating affected systems or disconnecting them from the network). The main phases of a good IRP are:
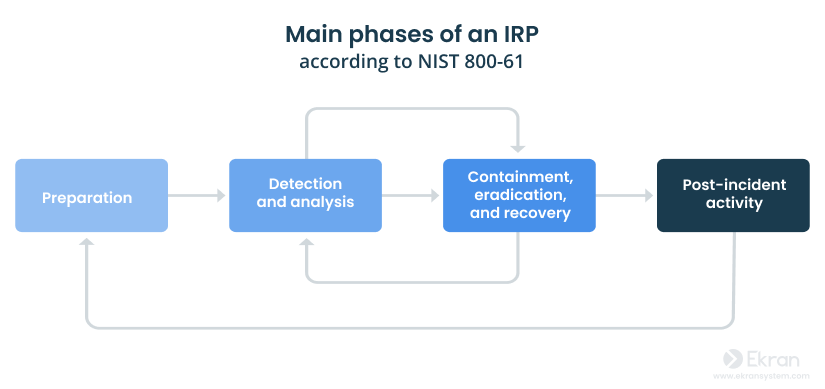
After your incident response plan is ready, don’t forget to regularly review and update it to ensure it’s effective and relevant to the current security landscape.
10. Mitigate insider threats
Prevention is better than cure.
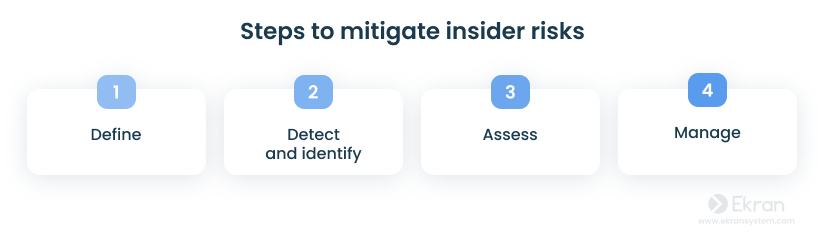
To mitigate potential insider threats before they escalate into serious security incidents, you need to follow a series of key steps: define, detect and identify, assess, and manage.
- Define — Develop an effective insider threat mitigation program to define what constitutes an insider threat.
- Detect and identify — Detect and identify individuals who may pose an insider threat.
- Assess — Assess the level of risk that identified individuals pose.
- Manage — Proactively manage insider threats to prevent harmful events and effectively mitigate their consequences.
How can Syteca minimize insider threats?
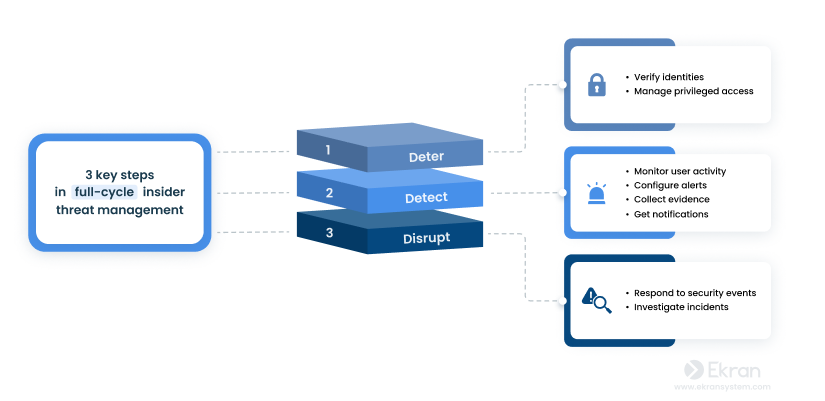
Being an all-in-one insider risk management solution, Syteca can become a powerful tool for insider threat protection within your organization. The platform provides a wide range of insider threat protection tools, from user activity monitoring to reporting, auditing, and automated incident response. Syteca supports the 3D rule (deter, detect, disrupt) by implementing a full-cycle security strategy that:
- Deters potential attackers
- Detects security threats in real time
- Disrupts security incidents before they can cause significant damage
Deter
By incorporating Syteca, you can benefit from granular access management for both privileged and general user accounts. The Syteca platform provides complete control over user identity thanks to comprehensive privileged account and session management functionality, two-factor authentication, password management, as well as accessing request and approving workflow. That is to say, Syteca can empower you with the necessary controls to secure critical endpoints and gain full visibility over all user accounts.
Detect
Syteca allows security personnel to monitor user activity on target endpoints, log all user sessions, record RDP sessions, and investigate any abnormal behavior or security incidents. The platform complements continuous user monitoring with advanced capabilities such as session video recording, key episode search, offline monitoring, and client protection.
The system detects potential insider threats through highly configurable real-time alerts. Alerts can be generated by an AI-powered user and entity behavior analytics (UEBA) module [PDF] or customized by security officers.
User Activity Monitoring (UAM) Software
Disrupt
Syteca provides security teams with real-time notifications and contextual information so they can not only immediately detect but also disrupt any potential insider threats. The platform includes a wide range of incident response options such as warning and blocking a user, killing the process that triggers an alert, and alerting the security team about a connected USB device and blocking it.
Also, Syteca lets you investigate security incidents thanks to an advanced reporting system that covers crucial data including visited URLs and launched apps (with time spent using them), captured keystrokes, executed Linux commands, plugged-in/blocked USB devices, and more.
Insider Threat Management Software
Conclusion
Ultimately, insider threats can cause lots of damage to your organization’s operations, reputation, and financial stability. Safeguarding your organization against insider threats should be an essential part of your cybersecurity strategy.
Syteca is an all-in-one solution to help you implement best practices for insider risk management and protect your organization against security threats. Its advanced features include user identity management, continuous user activity monitoring, reports and analytics, customizable alerts and real-time incident response, and more.
If you would like to gain complete visibility over user activity and attain effective protection against insider threats, Syteca may be the solution you’re looking for.





