Education is a strictly regulated industry in which robust cybersecurity protection is a must. Data breaches can cost a fortune for schools and universities, since the loss of students’ personal information and other critical data brings reputational damage alongside fines for regulatory non-compliance.
In the US in 2019 there were 348 publicly disclosed K-12 school-related cybersecurity incidents — triple the number in 2018. In this article, we explain the importance of cybersecurity monitoring for educational institutions, explore the main laws and standards that such organizations should meet in the US, and offer a strategy for establishing an efficient monitoring process.
Cybersecurity threats in the educational sector
The US education system is decentralized and both public and private educational institutions have to comply with relevant federal and state laws and regulations.
Private educational institutions are more autonomous and self-governed than public ones. Still, since the education industry is strictly regulated, states have oversight of both public and private schools.
Strict security requirements oblige schools, colleges, and universities to establish strong cybersecurity protections. However, applied measures are often not enough to protect sensitive data from breaches and leaks.
Insufficient protection often leads to multiple incidents and data breaches, putting at risk students’ sensitive information along with an institution’s reputation. According to the Verizon 2020 Data Breach Investigations Report, the educational services industry suffers from phishing attacks, malware via websites, and miscellaneous errors.
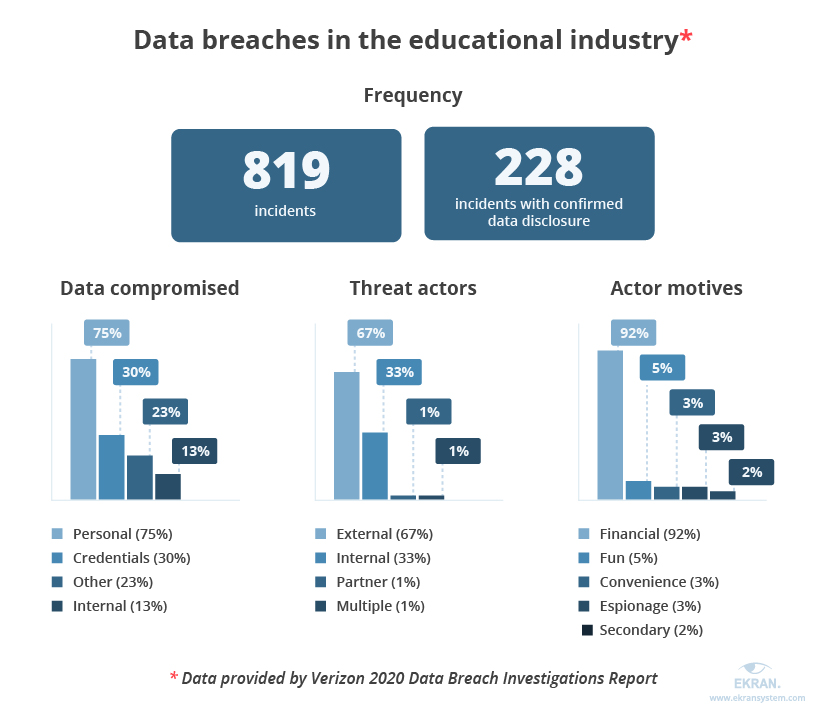
One of the incidents took place in the San Dieguito Union High School District, where unusual activity was spotted with certain employee email accounts. An investigation confirmed that the affected accounts had access to personal information stored in the school’s system: home addresses, Social Security numbers, medical information, and more.
The best way to detect and immediately respond to such incidents is to ensure robust cybersecurity monitoring. Let’s take a closer look at the benefits that cybersecurity monitoring provides to educational institutions.
Increase Employee Productivity with User Activity Monitoring
The importance of cybersecurity monitoring
Cybersecurity monitoring is the process of continuously observing an organization’s security posture to provide real-time visibility of all devices and systems within a monitored environment. Monitoring networks and devices is essential for educational institutions since it can prevent cybersecurity incidents and help you spot abnormal activity.
Cybersecurity monitoring allows organizations to receive valuable insights into user activity and check whether employees and students are following cybersecurity rules when interacting with an organization’s systems and devices.
Constant monitoring helps educational institutions keep their critical data and assets secure and allows them to:
- detect cyber threats, data breaches, and attacks in their infancy
- mitigate threats before they cause damage
- reduce attack response times
- comply with industry cybersecurity regulations and standards.
Cybersecurity monitoring consists of four steps:
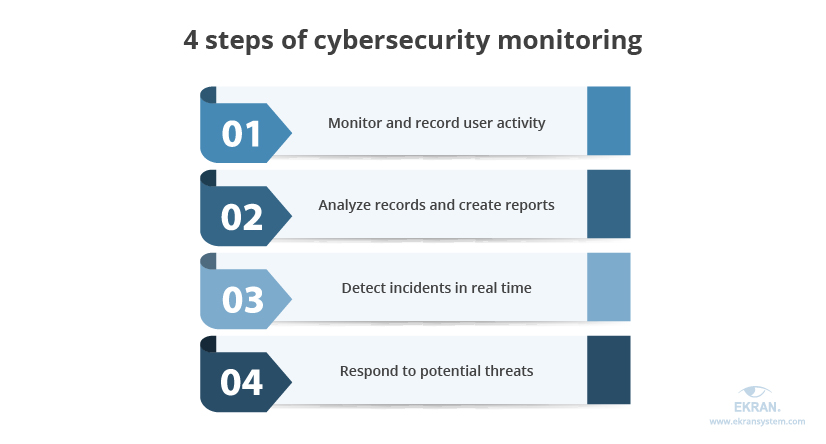
1. Monitoring and recording user activity. Monitoring user sessions is essential to know what resources employees and students access and how they interact with data. In case a cybersecurity incident occurs, records of monitored user sessions can be used to find the source of the attack and speed up the investigation. Also, users tend to behave more carefully when they know their activity is being watched.
2. Analyzing records and creating reports. User session recording tool helps to conduct in-depth analysis and generate reports on recorded sessions. They are needed to identify resources accessed by users and check whether accessing such resources is safe for the organization’s network. Also, analyzing records and reports gives insights into the frequency of accessing critical data and can help organizations spot abnormal user activity.
3. Detecting incidents in real time. Each time a user accesses a suspicious website or takes an action that contradicts cybersecurity rules (e.g. tries to copy or change sensitive data), a security officer can immediately be notified so they can check whether this is a malicious activity or an unintentional error.
4. Responding to potential threats. Once suspicious activity is detected, cybersecurity officers or administrators should respond by warning users or denying access to certain systems. Modern security solutions for educational institutions also allow for setting automated incident responses to react to threats right away. An instant response is a must because it can prevent a real cybersecurity incident and save sensitive data from leaks or damage.
With this information in mind, let’s discover how you can establish efficient cybersecurity monitoring in your organization.
4 steps for arranging efficient cybersecurity monitoring
Keeping an organization’s digital and information systems and networks secure requires proper planning. You should revise and check your current cybersecurity strategies to see whether they:
- ensure the protection of all critical data
- comply with relevant regulations
- define criteria for efficient monitoring software.
To establish a proper level of cybersecurity in an educational institution, you should explore guides and recommendations created by specialized media portals and organizations:
- Cybersecurity Considerations for Institutions of Higher Education [PDF] by the Readiness and Emergency Management for Schools (REMS) Technical Assistance (TA) Center
- Cybersecurity Considerations for K-12 Schools and School Districts [PDF] by the REMS TA Center
- Breach Readiness: Strategies to Secure Schools by the Center for Digital Education
- Increase Visibility to Better Manage Student Safety by the Center for Digital Education
Let’s take a look at the four major steps to arrange robust cybersecurity monitoring in schools, colleges, and universities.

1. Define what to monitor
Schools, colleges, and universities must keep an eye on three main aspects of cybersecurity:
- Sensitive information that requires robust protection
- Management and educational systems used within the institution
- Users who have access to the organization’s data
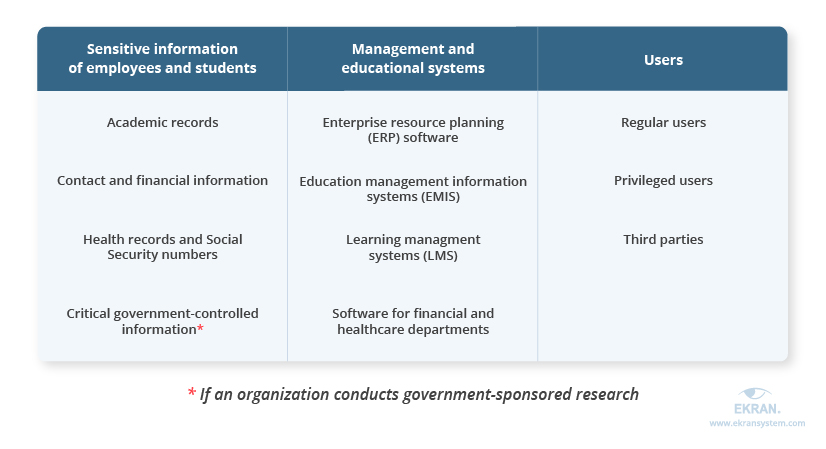
Since educational institutions handle silos of data, the first thing to do is to define all the sensitive information that must be protected and ensure that access to this data is strictly limited to authorized users.
The next step is to secure management and educational systems such as enterprise resource planning systems, education management information systems, learning management systems, and software for financial and healthcare departments. Such solutions not only store valuable information but help employees handle their work and help students study. If such software gets compromised, both managerial and educational processes will be disturbed.
Last but not least is controlling permissions and monitoring the accounts of users who can access data and therefore potentially pose a threat to its security. Even regular users whose access rights are limited to the extent of their daily tasks can cause harm unintentionally by accidentally deleting files or interacting with a phishing email from a school’s computer. Also, users can act as malicious insiders and steal or damage confidential information on purpose.
It’s also essential to remember that the more privileges users have, the more harm they can do. Therefore, you should pay special attention to monitoring the activities of privileged users and third parties.
2. Make sure to comply with laws and regulations
Once you’ve figured out what data you should monitor, it’s easier to define the requirements you have to comply with.
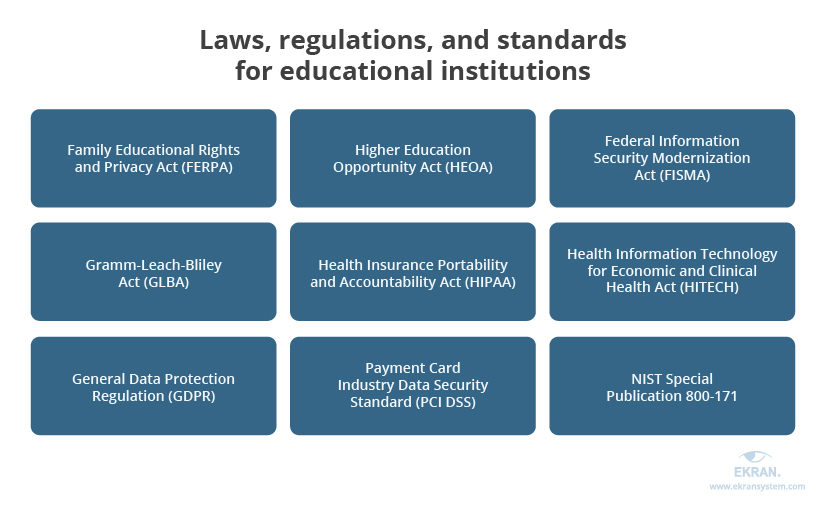
The two most important laws for US educational institutions are:
- the Family Educational Rights and Privacy Act (FERPA), a federal law that protects the privacy of students’ educational records. FERPA applies to all schools that receive funds under an applicable program run by the US Department of Education.
- the Higher Education Opportunity Act (HEOA), a law that requires institutions of higher education to improve safety of their systems and networks and secure students’ sensitive data.
Apart from these two laws, educational institutions may need to comply with financial, healthcare, and cybersecurity standards, since they usually have school-based health centers and process payments. Also, US-based institutions that educate students from Europe or have employees from the EU should comply with the General Data Protection Regulation (GDPR).
Cyber Security Threats in Education Institutions
3. Update your cybersecurity policies
Make sure to introduce clear cybersecurity policies to provide guidance for the protection of critical data and assets. Such policies are crucial for every educational organization since they cover the acceptable and secure use of systems and data. They also educate users about ground rules and consequences of violating them.
A standard cybersecurity policy usually includes the following sections:
- Basic information on types of data an organization handles
- Measures an organization applies to secure critical data, IT assets, and infrastructure
- Information about state and federal laws with which an organization should comply
- Departments responsible for cybersecurity system maintenance
- Information about user activity monitoring and recording
- Password management practices
- Information about cybersecurity incident management
- User guidance on the secure use of organizational systems
- Instructions on user actions when a cybersecurity incident occurs and contact information of the support team
By explaining the way an organization handles and protects data security, you can educate employees and students and prevent incidents.
4. Choose and deploy monitoring software
To track user activity with sensitive data, organizations deploy specialized software for cybersecurity monitoring. Such software monitors and records user and entity activity, analyzes the gathered data, and provides detailed cybersecurity reports on the state of monitored systems and endpoints.
To ensure robust protection, make sure to choose monitoring software that offers the following features:
- User activity monitoring and recording on computers, servers, and in virtual environments
- Web and email monitoring to secure browsing and protect networks and devices against phishing, malware, and ransomware
- Multi-factor authentication to validate users and protect access in case passwords are stolen
- Data encryption and backups to secure data from malicious actors and restore sensitive data in case of an incident
- Anomaly detection to identify unusual behavior that may be a sign of an unauthorized user who has managed to get access to a system
- Real-time alerts to notify security officers about potential incidents so they can take measures before a malicious user causes harm
You can potentially deploy several solutions for education security monitoring with limited features to cover all the functionality mentioned above. However, it’s best to focus on all-in-one software that can provide efficient monitoring and is convenient to use.
12 Best Cybersecurity Practices in 2020
Using Syteca for cybersecurity monitoring
Syteca is a full-cycle insider threat management platform that effectively deters, detects, and disrupts insider threats. It successfully monitors user activity, detects cybersecurity incidents in their infancy, and enables you to immediately respond to cyber threats.
With a Syteca deployment, you can record all user sessions and search through session records by URLs, application names, keystrokes, etc. Sytecaempowers you to monitor the activity of privileged users and third parties to make sure they don’t misuse elevated access rights.
You can also use Syteca to prevent unauthorized access to sensitive data with robust access management and control the access level of each user. All sensitive information is secured with built-in encryption of passwords, credentials, monitoring records, and other data.
Additionally, with Syteca you can leverage the opportunity to instantly detect abnormal activity and respond to it by sending a warning to a user or blocking a session. Customizable reports include only the information you require: user activity, keystores, visited URLs, etc. Plus, you’ll be able to easily investigate incidents using data gathered in a tamper-proof format that can be used as evidence.
Finally, Syteca helps you comply with various standards and regulations including NIST 800-53, SWIFT CSP, HIPAA, GDPR, FISMA, and PCI DSS.
Privileged Password Policy Compliance Overview: NIST 800-63, HIPAA, PCI DSS, GDPR
Conclusion
Schools and universities in the United States store financial, health, and personal information on their employees and students. Since such valuable data attracts cybercriminals and malicious insiders, educational institutions require flawless cybersecurity.
Securing educational institutions with robust monitoring is one of the most efficient ways to protect sensitive data. It allows organizations to monitor and record user activity, analyze records, create helpful reports, and detect and respond to incidents in real time before severe damage is done.
To achieve efficient cybersecurity monitoring, organizations need to identify data and systems to protect and users to keep an eye on, update policies, and choose the most suitable monitoring software.

With Syteca, you can cover multiple monitoring tasks and efficiently protect your data from malicious insiders. Enjoy your free trial to explore the full range of opportunities provided by the Syteca monitoring solution.




