Protecting your sensitive data and other critical assets requires establishing secure access to them in the first place. Lots of organizations do this by protecting their remote servers and corporate systems with SSH keys. However, even SSH keys can be compromised and abused by malicious actors.
In this article, we talk about SSH keys and their role in secure authentication processes as well as about the benefits of effective SSH key management. Also, we offer six useful practices that will help you secure your digital keys.
SSH key authentication management basics
What is SSH key management?
Secure Socket Shell (SSH) key authentication is a convenient and secure way to connect computers over the internet. It allows employees (mostly admins) to remotely access another computer, server, or network without continually logging in using a username and password. With SSH, authorized users can manage applications, execute commands, and move files from one computer to another in a fast and secure manner.
Organizations benefit a lot from using SSH key security authentication, since it secures access to servers and encrypts traffic that’s in transit between a client and a server. To connect to a remote machine, users have to generate a pair of digital keys:
- A public key that can be shared with others
- A private (or identity) key that should be kept secret by the authorized person
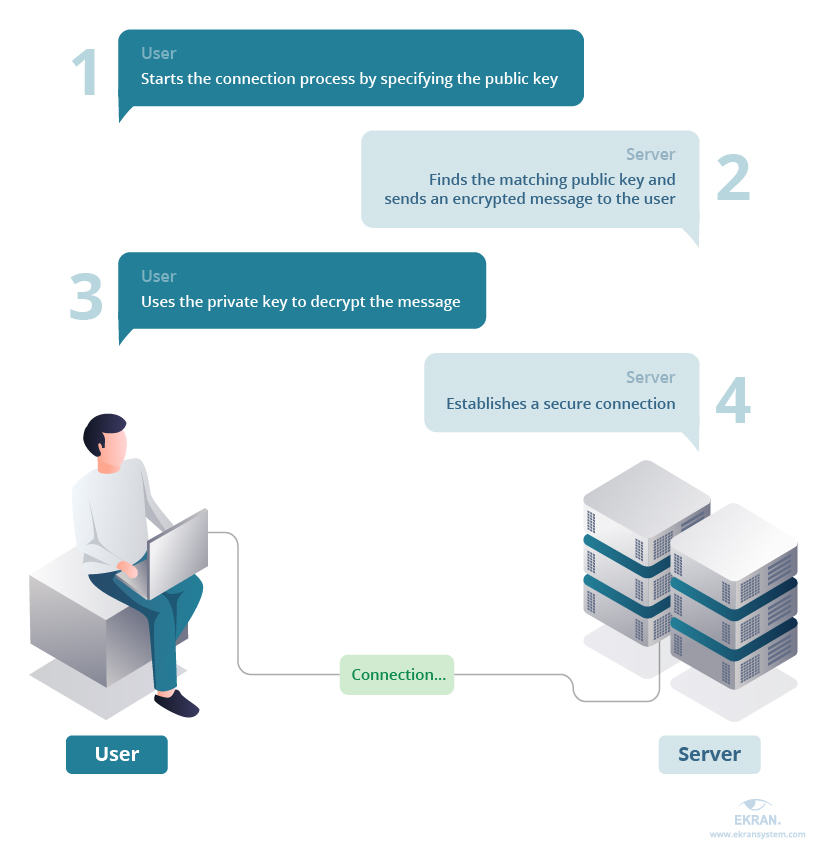
A simplified view of the SSH authentication process
You can ensure proper protection of keys with SSH key management — a combination of practices, policies, and tools for establishing secure SSH key usage routines within an organization. SSH key management can significantly enhance corporate cybersecurity by protecting networks and systems from both external and insider attacks. It can also help an organization comply with cybersecurity standards, laws, and regulations.
At its core, SSH key management consists of four main tasks:
- Properly provisioning SSH keys
- Keeping track of an organization’s public and private keys
- Monitoring SSH key use
- Protecting pairs of SSH keys

To accomplish these goals, system administrators apply various methods to generate, store, use, rotate, revoke, and terminate keys in a way that protects them from unauthorized users and cybercriminals.
The importance of efficient SSH key management
What happens if you fail to control your digital keys?
Since SSH keys provide access to sensitive resources and data, you should prevent them from falling into the wrong hands. Also, various laws, regulations, and standards like HIPAA, the GDPR, and PCI DSS contain specific requirements for secrets management, and SSH keys are a type of secret.
Without centralized control, you can’t know how many SSH key pairs are in your organization’s network, who uses them, and how. And if you mismanage your SSH keys, it will create severe cybersecurity risks:
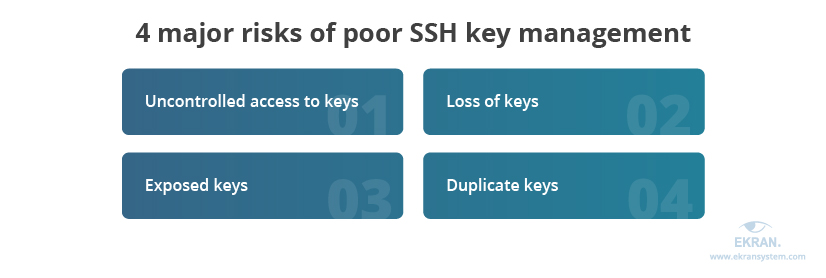
1. Uncontrolled access to keys. Malicious actors can abuse unprotected SSH keys to gain access to privileged accounts. Here are a few scenarios of how this may happen:
- If users can create their own authorized SSH keys, malicious insiders may use this opportunity to generate backdoor keys.
- If an organization doesn’t monitor and rotate SSH keys, terminated employees can still access sensitive data long after they leave a position or a company.
2. Loss of keys. An important detail about SSH keys is that they are static, meaning they don’t have an expiration date. Combine this with a lack of proper secret monitoring routines and you are likely to end up with a number of legitimate SSH keys that have been misplaced or simply forgotten. Keys that are no longer actively used and the location of whose corresponding public or private key is unknown are called orphaned keys.
The longer keys are in existence, the harder it becomes for security teams to identify their purpose and to rotate them to maintain security. Also, if there are no requirements for key management and inventory procedures, you may lose access to public key storage when you’re patching, upgrading, reusing, or reinstalling servers.
3. Exposed keys. Without clear SSH key management rules, there’s always a risk of key exposure. SSH keys can be exposed either through misplacement or through unauthorized sharing.
For example, administrators can embed static SSH keys into an application’s code or scripts, making the application vulnerable to hacker attacks. Or your employees might share keys with each other using messengers and other insecure channels.
4. Duplicate keys. Without strict policies for generating SSH keys, admins may often replicate keys to share access to servers and infrastructure components among a group of employees. Duplicate keys share the same key fingerprint (a special checksum generated based on the public SSH key).
Duplicating keys significantly complicates the process of rotating a single key or revoking it without breaking other SSH key relationships. Also, availability of duplicate keys may increase the chances of malicious insiders gaining access to and misusing those keys.
Secrets Management: Importance, Challenges, Best Practices
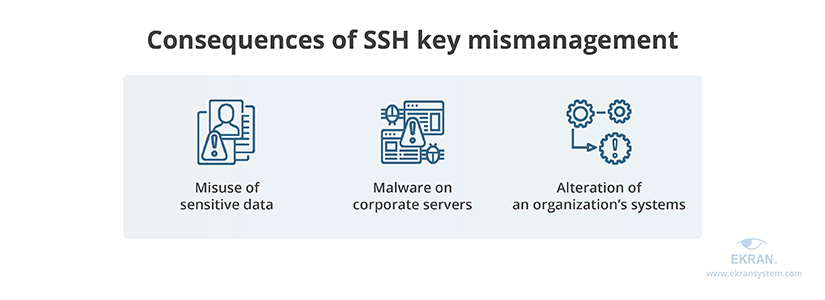
All of the risks mentioned above may lead to a situation where an attacker can gain access to digital keys, resulting in misuse of data, installation of malware on corporate servers, and altering the configurations of an organization’s systems.
To avoid these cybersecurity issues, you need to enhance your SSH key management. Doing so will help you:
- Account for all generated SSH keys
- Ensure that no extra keys are generated except for valid reasons
- Know who accesses keys and when
- Avoid reusing keys across systems and users
- Immediately change or revoke access to keys
But how exactly can you build an efficient SSH key management strategy? In the next section, we offer six best practices that can help you achieve this goal.
6 SSH key management best practices
Building an SSH key security strategy is a great way to bring key generation and use under control. However, it may be challenging to figure out where to start and what activities to perform. To make this process a bit easier for you, we’ve outlined six best practices that will help you efficiently manage SSH keys within your organization.

1. Find and inventory all SSH keys
You can’t protect those SSH keys whose existence you don’t know about. So the first step in managing SSH keys is finding all existing keys and associating them with users and servers.
To do that, you can use various tools for digital key management. Using such tools, you can discover all existing keys within your IT infrastructure and learn what servers, machines, or systems they have access to. Thus, you can find potential vulnerabilities like duplicate or orphaned keys and fix them, as well as identify who’s using what keys to access which systems.
Once you’ve found all existing keys, make sure to:
- Inventory all your digital keys
- Associate every key with the users and machines it corresponds to
- Delete unused and unneeded keys
- Move all keys to one centralized and protected storage
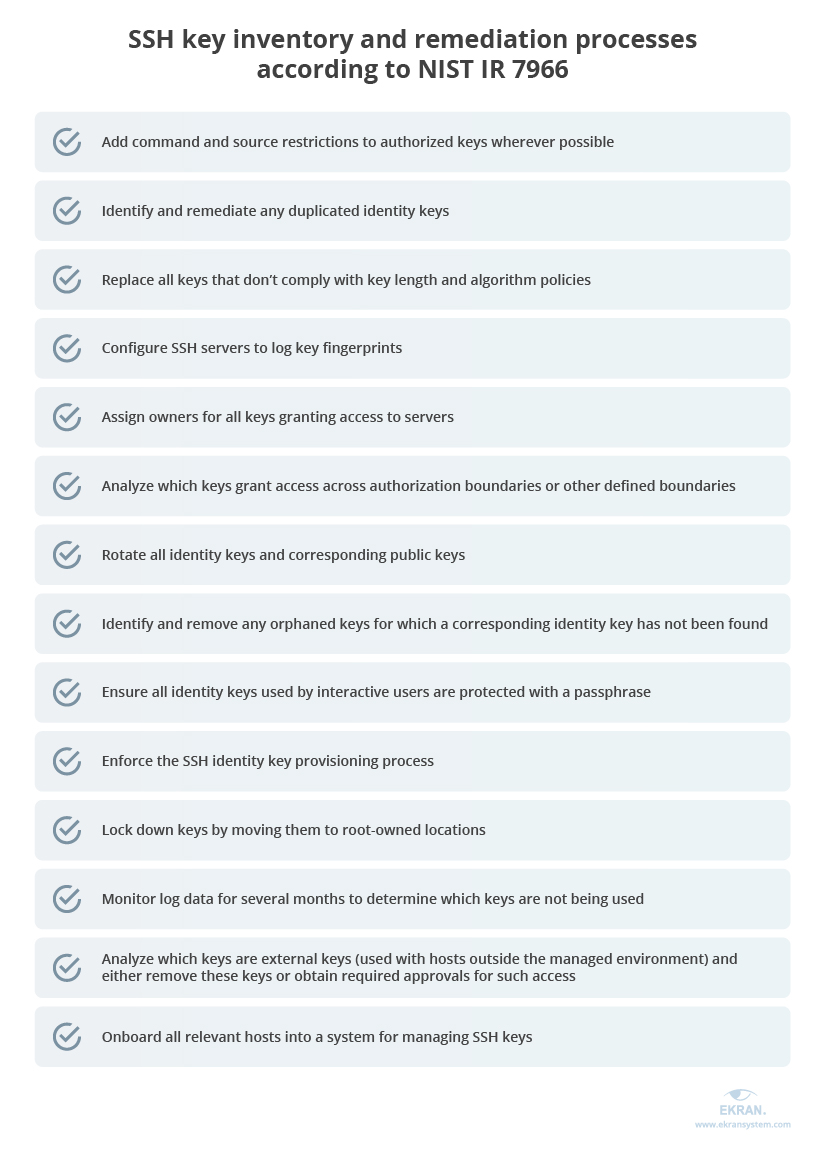
According to NIST IR 7966, SSH key inventory and remediation typically includes the following processes:
2. Implement the principle of least privilege
Privileged users should always have access rights only to the data and systems they need for work purposes.
To make this happen, configure individual SHH keys for these employees that allow them to access only the systems or machines they need to perform their duties. Also, make sure to review access rights when employees shift to another position. Avoid shared accounts because they make it impossible to identify who used a pair of keys.
3. Eliminate hard-coded and old SSH keys
As we mentioned earlier, SSH keys can be embedded in code or scripts, which can create dangerous backdoors for malware and hackers to exploit. Make sure to check your code for embedded SSH keys, bring them under centralized management, and remove them from applications.
Old keys include orphaned and forgotten unaudited keys that can be exploited by cybercriminals. To avoid their appearance, it’s essential to:
- Terminate access to remote servers for any accounts associated with employees that leave an organization
- Keep track of all generated SSH keys
- Reduce the number of duplicate keys
7 Best Practices to Prevent Data Theft by Departing Employees
4. Establish SSH key rotation
Since keys are static, rotating them is necessary to ensure the security of SSH keys. This will help you eliminate chances for malicious actors to compromise and exploit your digital keys.
SSH key rotation means replacing a private key with a newly generated key and updating public keys correspondingly. Although NIST IR 7966 recommends using this method, it also warns you that key rotation can break external keys (keys that are used from outside the managed environment). Therefore, when rotating external private keys, make sure to notify the other side so they will ensure the rotation of the public key. Otherwise, you’ll lose access to the external host.
5. Set clear rules for SSH key use and management
Implement an SSH key management policy or make sure your current security policy has all the rules for proper SSH key management. Policies and procedures must establish consistent baseline requirements across all environments where SSH keys are used. These policies should clearly spell out roles and responsibilities to prevent security lapses.
Key questions to cover with SSH security policies and procedures:
- Who can create keys and for what purposes?
- What is the procedure of requesting a pair of keys for an employee?
- How should keys be stored?
- How many users can be associated with a single key?
- How often should keys be rotated?
- What should happen to keys when the user associated with them leaves the organization or switches to another position?
Also, you have to make sure that all SSH stakeholders like system administrators, security specialists, and business application owners are well-educated on SSH security policies and procedures.
How to Secure a System Administrator’s Privileged Accounts: 7 Best Practices
6. Continuously monitor and audit SSH key use
Thorough digital key monitoring will help you ensure that employees are following all established procedures for SSH key management and help you detect unauthorized access to keys.
NIST IR 7966 recommends organizations provide continuous SSH key monitoring by doing the following:
- Verifying that keys are deployed according to the organization’s policies
- Configuring notifications for detection of unauthorized keys
- Making sure out-of-compliance situations can be automatically remediated (i.e. by rolling back accidental changes or deletion of keys)
- Tracking and monitoring key use and discovering unused keys
- Identifying keys that don’t comply with corporate policies
Also, check whether you meet all necessary compliance requirements for secrets management. Depending on the industry your organization is working in, you may need to pass HIPAA, GDPR, PCI DSS, FISMA, or SWIFT CSP audits (among many others) on a regular basis.
Meeting IT Compliance Requirements
Managing secrets with Syteca
With Syteca’s privileged access management (PAM) solution, you can securely deliver secrets and rotate passwords as well as configure, encrypt, and manage privileged user credentials.
Our solution offers you a rich set of secrets management capabilities for working with:
- Local Windows admin passwords
- Windows Active Directory secrets
- SSH/Telnet keys (for UNIX environments)
- And more
Syteca also offers organizations the opportunity to audit, monitor, and rotate SSH keys for Unix accounts on a regular basis to reduce the risk of their being compromised. Using Syteca’s PAM functionality, you can effectively manage various types of secrets alongside controlling, user activity monitoring, keystroke tracking, and auditing privileged accounts.
Conclusion
The more unmonitored SSH keys exist in your network, the higher the chances of malicious insiders or hackers gaining privileged access rights and misusing them without being caught. Luckily, you can reduce those chances by organizing a robust SSH key management strategy.
To take them under control, it’s essential to discover and inventory all existing SSH keys. Clearly spell out the rules for key generation, use, rotation, and termination in your corporate cybersecurity policies. Also, don’t forget to check whether your security practices towards SSH key management align with industry cybersecurity requirements. These steps will help you create an effective SSH key management strategy.
Syteca is insider risk management software that helps you deter, detect, and disrupt insider threats in a secure and convenient way. While managing privileged access and identities, our platform allows you to comply with requirements and establish secure SSH key management. Within Syteca’s password management functionality, you can add Unix account SSH keys and ensure their automatic or manual rotation.
Request a 30-day trial to see how Syteca can help you manage privileged access by securely handling SSH keys!




