Lawyers constantly handle sensitive data that attracts hackers and malicious insiders. Every security breach leads to reputational losses, remediation costs, and penalties. That’s why cybersecurity at law firms is regulated by strict IT laws and requirements.
Complying with all necessary requirements and implementing protection measures that fit your organization is challenging. In this article, we overview the reasons for and types of security breaches in legal organizations and show you how to prevent them by implementing best practices for complying with IT requirements.
Security threats in the legal industry
Why is legal data under attack?
The number of cybersecurity breaches in the legal industry has been growing for the past three years. According to the American Bar Association’s 2019 Legal Technology Survey Report, 26% of law firms report they’ve suffered from a breach at some point in their history. Another 19% say they don’t know whether their organization has been breached.
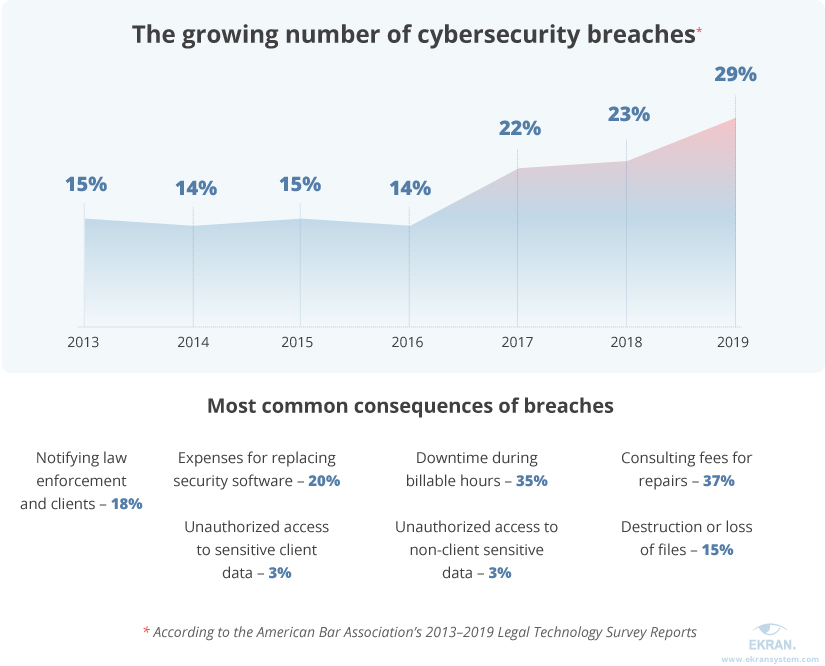
One of the most common reasons for data breaches is an insider attack. A recent study shows that 96% of IT leaders in the legal industry believe an insider breach to be a significant risk for their organization.
What does insider threat mean?
Insider threats come from within an organization in the form of employees and third-party contractors. These entities may intentionally or unintentionally leak sensitive information or provide hackers with access to it. Insider threats are as dangerous as outside hacker attacks because insiders have good knowledge of a law firm’s cybersecurity measures and the sensitive data a firm stores.
There are several key motivations for malicious insider activity:
- Espionage — Breaching data on behalf of market competitors or other states
- Hacktivism — Leaking sensitive data for political and social reasons
- Sabotage — Doing damage as a disgruntled employee
- Personal gain — Stealing sensitive data for insider trading or opening a new law firm
Portrait of Malicious Insiders: Types, Characteristics, and Indicators
Usually, insider attacks on law organizations make headlines. The most well-known cases are the Panama Papers and the Paradise Papers — leaks of millions of classified documents that originated from two law firms. Those firms’ reputations were permanently damaged, and the clients of those firms had to spend a substantial amount of money mitigating the results of the leaks.
In 2019, the senior director of corporate law at Apple was charged with insider trading. He used protected company information, including financial reports, to trade Apple stocks during blackout periods when employees can’t legally trade. Interestingly, one of his responsibilities at Apple was to prevent employees from engaging in insider trading.
During 2020, seven law organizations suffered from ransomware attacks executed in the same way: hackers abused remote sessions and hijacked credentials of privileged users to plant malware. Then, the malware encrypted sensitive data stored on an organization’s servers until the organization paid the ransom.
All of these incidents could have been mitigated with strong insider threat management and data protection tools. Deploying such tools is the demand of many cybersecurity regulations for law firms. We take a look at the most important regulations in the next section.
5 Real-Life Cases When Employees Caused Data Breaches
Data protection compliance requirements to follow
What IT regulations should you follow?
Depending on your specialization, your law firm may work with various types of sensitive client information including personal, financial, and healthcare data. Each of these types of data is protected with security standards, laws, and regulations. Also, there are recommendations from key cybersecurity and legal organizations that law firms should follow.
Failure to comply with these cybersecurity compliance requirements may prove fatal for a law company. It can not only lead to legal trouble and investigations but can also damage the company’s reputation and cause a loss of clients. Let’s review key regulations, laws, and standards that apply to law firms.

US-based law firms have to follow the Model Rules of Professional Conduct developed by the American Bar Association — the biggest professional organization for lawyers in the US. The American Bar Association forms rules that make legal services ethical, efficient, and safe. Its Formal Opinions 477R and 483 describe mechanisms required to monitor for data breaches, implement security measures to stop them, notify clients of a breach, and remediate the damage of a breach. Both Formal Opinions oblige lawyers to “make reasonable efforts to prevent the inadvertent or unauthorized disclosure of, or unauthorized access to, information relating to the representation of a client.”
The National Institute of Standards and Technology (NIST) established and maintains Special Publication 800-53, a complete set of cybersecurity practices and regulations for US federal agencies. Complying with these regulations is beneficial for all organizations: it verifies the effectiveness of implemented protection measures and provides a competitive advantage.
How to Pass IT Compliance Audit
Legal companies that operate in the EU or manage data of EU residents have to comply with the General Data Protection Regulation (GDPR). This document determines which personal data of EU residents should be protected and enforces strict security measures. Non-compliance with the GDPR can lead to severe fines up to 4% of annual global turnover or €20 million. Our checklist for GDPR compliance can help you meet its requirements.
Also, each country and each US state has its own data protection laws and recommendations. For example, law firms in California have to take into account the California Consumer Privacy Act, while in New York, law firms have to account for The New York State Department of Financial Services regulations; in the UK, there’s the Data Protection Act.
As we mentioned, there are industry acts and standards that describe the necessary data protections for specific types of data:
- HIPAA for healthcare information
- PCI DSS for financial and credit card data
- SOX for accounting and investor information
- And more
The list above look like too much to take in, but in fact, most cybersecurity standards and regulations contain similar requirements. In the next section, we’ll take a look at nine tips to improve law firm cybersecurity.
Meeting IT Compliance Requirements
9 security best practices for data security compliance
Comply with regulations easily and effectively.
Improving cybersecurity controls may seem time-consuming and costly, but it’s still easier and safer than dealing with a security breach. That’s why it’s best to implement security practices, policies, and tools that help to detect and mitigate a breach before it happens.
For the legal industry, the set of required practices includes the following:
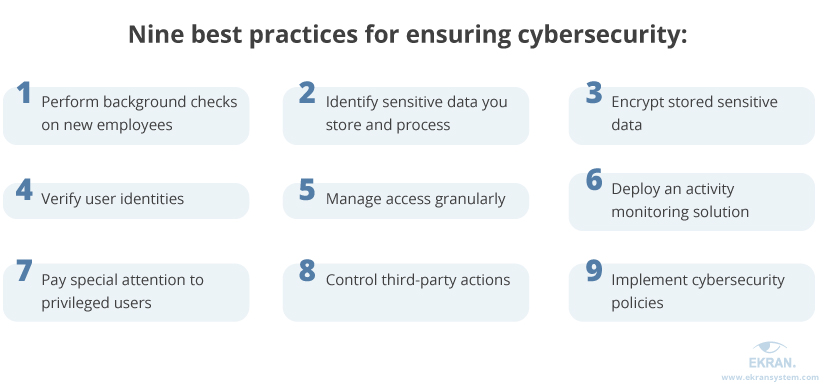
1. Perform background checks on new employees.
When hiring employees, the HR department has to check their backgrounds: previous employment, credentials, professional experience. Any difference between an employee’s resume and actual records may indicate dishonesty.
2. Identify sensitive data you store and process.
Law companies deal with tons of documents, and it’s impossible to ensure proper data protection before you detect which of those documents contain sensitive information. Such information includes:
- client and employee contact information
- payment and financial details
- health data
- lawsuit information protected with non-disclosure agreements
3. Encrypt sensitive data.
If a hacker or malicious insider obtains encrypted sensitive information, it will be impossible to read and use. To access such files, a user or server has to request access rights from a content owner (also a user or server). It’s best to encrypt data both at rest and in transit to ensure complex protection.
To further enhance the privacy of sensitive information, consider pseudonymizing personal data to prevent individual identification.
4. Verify user identities.
Hackers often steal user credentials to obtain elevated access rights. Also, employees may use shared accounts or colleagues’ profiles. Both cases present a security threat that can be mitigated with an identity verification tool such as two-factor authentication. It checks an additional factor (smartphone, biometric data) in addition to a password to positively authenticate a user.
5. Manage access granularly.
The idea of several access levels to corporate data is well-established in the legal industry. With digital data protection, it works the same way: security officers manage employees’ access to sensitive information and carefully adjust access level to the needs of each employee.
6. Deploy an activity monitoring solution.
A continuous user activity monitoring solution provides you with data on each action inside your protected perimeter. Such software deployed in a law firm monitors servers and endpoints, alerts security officers of suspicious user activity, records daily operations, and provides the means to review any security incident.

7. Pay special attention to privileged users.
Privileged users have access to an organization’s critical data and infrastructure, and thus pose a greater danger than ordinary users. That’s why privileged users in law firms need to consider the capabilities of privileged account management platforms: password management, manual access request approvals, granular management of access permissions, and more.
8. Control third-party actions.
Attacking an organization through a third-party vendor is a common attack vector. Subcontractors usually have elevated access rights in the client’s environment, but they don’t always pay attention to security. To avoid such incidents, check a vendor’s compliance with cybersecurity standards and enforce access management and activity monitoring.
9. Implement cybersecurity policies.
An incident response plan and insider threat protection program are essential security policies for a law firm to develop. They describe procedures for managing and mitigating threats, helping you keep security measures at a high level, avoid confusion during a breach, and reduce breach reaction times.
Incident Response Planning Guideline for 2020
Deploying a dedicated cybersecurity solution can help you implement most of the cybersecurity practices for law firms mentioned above. The choice of the solution depends on the specifics of the information you work with. To secure the personal data of EU residents, choose GDPR compliance software, while proctection of US citizens’s healthcare data requires a reliable HIPAA compliance solution.
Ensure compliance with Syteca
Syteca is an insider threat management platform that allows you to create a full cycle of data protection:
- Control access to data
- Monitor user activity
- Respond to security breaches
- Investigate suspicious incidents
Syteca’s robust access management toolset includes features for building a role-based access control model, manually approving access, and managing user rights in a couple of clicks. A two-factor authentication tool allows for establishing a user’s identity by sending a verification code to a smartphone.
User activity monitoring functionality logs all actions of regular, privileged, and third-party users. You can review their sessions online or in records via a built-in YouTube-like video player. Records are coupled with a set of metadata (opened files, URLs, keystrokes, connected devices, etc.) to ease the search for a specific event and allow you to establish its context.
Alerts and notifications inform security officers about suspicious activity happening on monitored endpoints. Security officers get alerts via email when a user violates one of the default or custom security rules set in Syteca. Also, the AI-based user behavior analytics module informs security officers of abnormal user behavior in real time via an email that contains a description of the violation and a link to the corresponding session. Security officers can then analyze the incident and block the activity or the user.
If a security incident happens, you can investigate it and report it to your clients and government authorities. With the Syteca toolset, you can quickly detect and review incidents, analyze damage, and act to mitigate it. Sytecagenerates periodic and ad hoc reports in a forensic format to keep you informed of security incidents and provide evidence in court if necessary.
Insider Threat Software Comparison
Conclusion
Ensuring solid cybersecurity is a high priority for every law firm. It allows you to guarantee lawsuit confidentiality to clients, prevent security and insider breaches, and respond to suspicious incidents in a timely manner.
Complying with IT requirements is a good way to ensure that sensitive corporate data is properly protected. Various laws, standards, regulations, and directives describe security measures and best practices for law firms.
Syteca helps legal companies monitor each user’s action inside their environment, receive alerts on suspicious activity, and respond to them. Syteca is optimized for large enterprises, is simple to deploy, and comes with 24/7 technical support.
Start with a free trial to ensure your compliance with all data protection requirements in the legal industry!




