Identity Management
Manage identities. Control access. Mitigate insider threats. ALL-IN-ONE
What is identity management?
Identity management is the key you need to prevent the wrong people from accessing your critical assets. It’s an essential part of insider threat mitigation, helping to prevent compromised account access, keep employees from “borrowing” passwords from colleagues, and identify the people hiding behind shared and default accounts.
Important tasks of identity and access management (IAM) systems include:
- Authenticating and authorizing users in a secure yet convenient manner
- Personalizing shared and default accounts and assigning actions to specific users
- Controlling access permissions in a granular, time-based, and purpose-based manner
- Monitoring and auditing the activity of authenticated users
- Ensuring immediate response to security incidents
- Meeting compliance requirements and implementing security best practices
Syteca delivers an essential identity management toolset, helping you with these tasks and ensuring compliance with multiple security regulations as well as NIST security controls.
Syteca identity management solutions
Syteca identity management software addresses an organization’s vital need for reliable validation of users’ identities and the unambiguous attribution of each action to a specific person. Our flexible identity management platform is seamlessly integrated with access control, user activity monitoring, and incident response functionality.
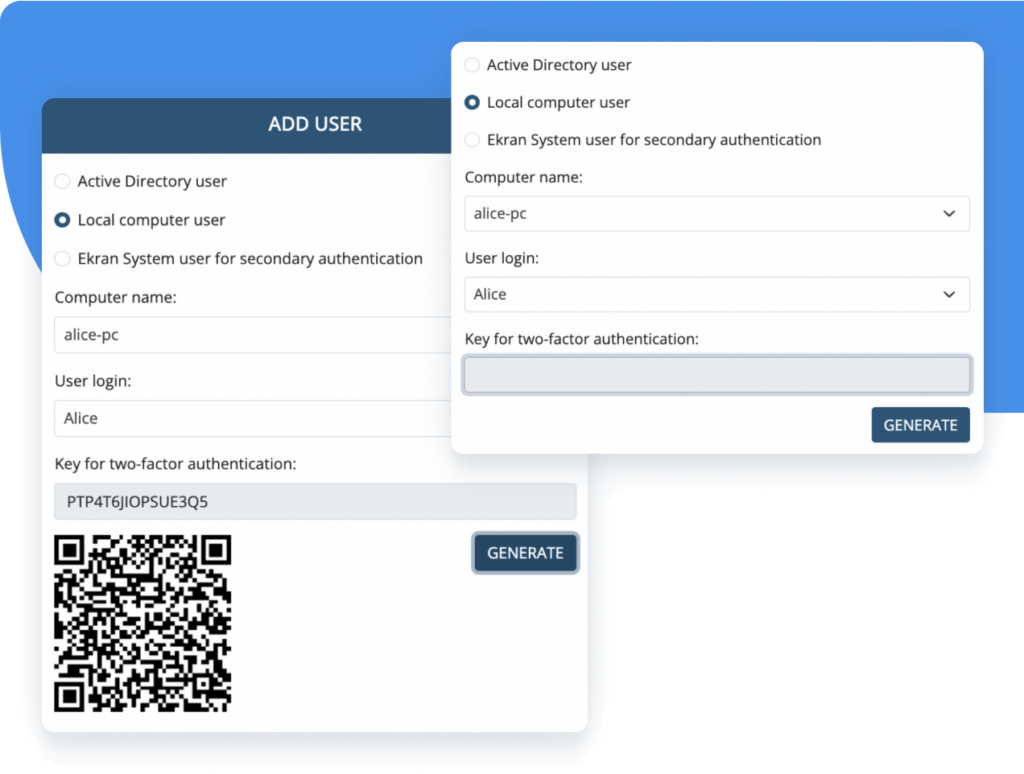
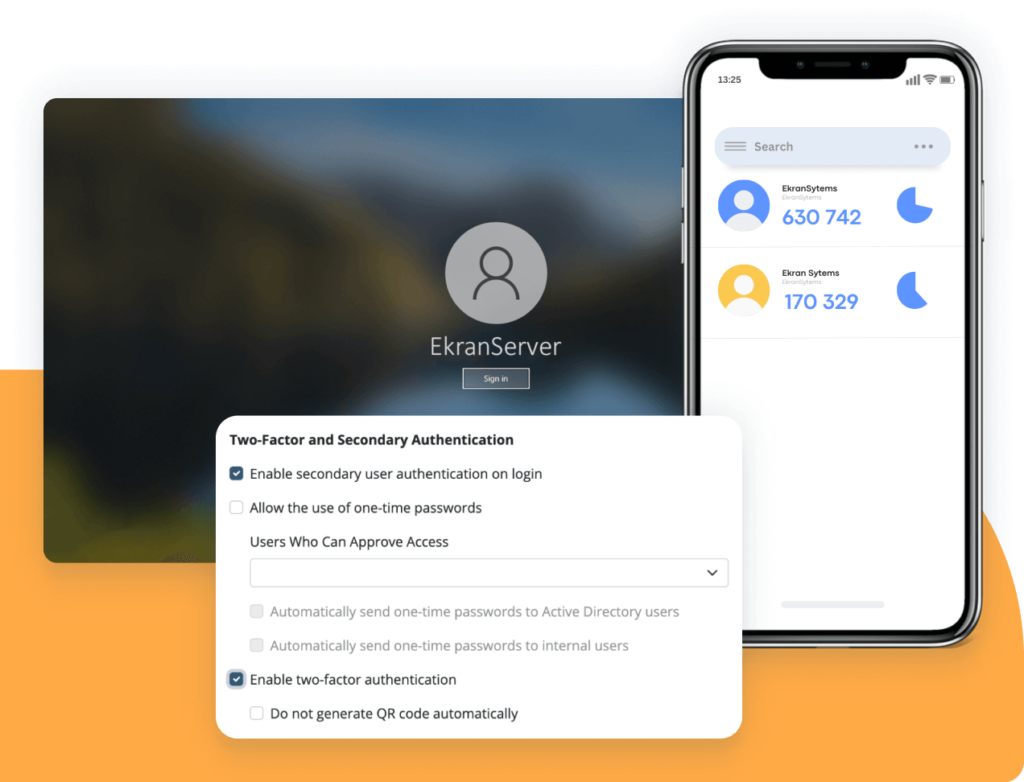
Multi-factor authentication
Mitigate the risk of intrusions with the help of our two-factor authentication (2FA) tool. 2FA serves as an additional confirmation that the person attempting to access your critical assets is who they claim to be.
This feature adds one more level of protection to your critical endpoints and sensitive data by combining two factors:
- Knowledge (user credentials)
- Possession (authorized mobile device)
Syteca applies a proven time-based one-time password scheme as an alternative to costly SMS and physical tokens. Our 2FA tool can be deployed on any Windows and Linux server or workstation under any of our licenses.
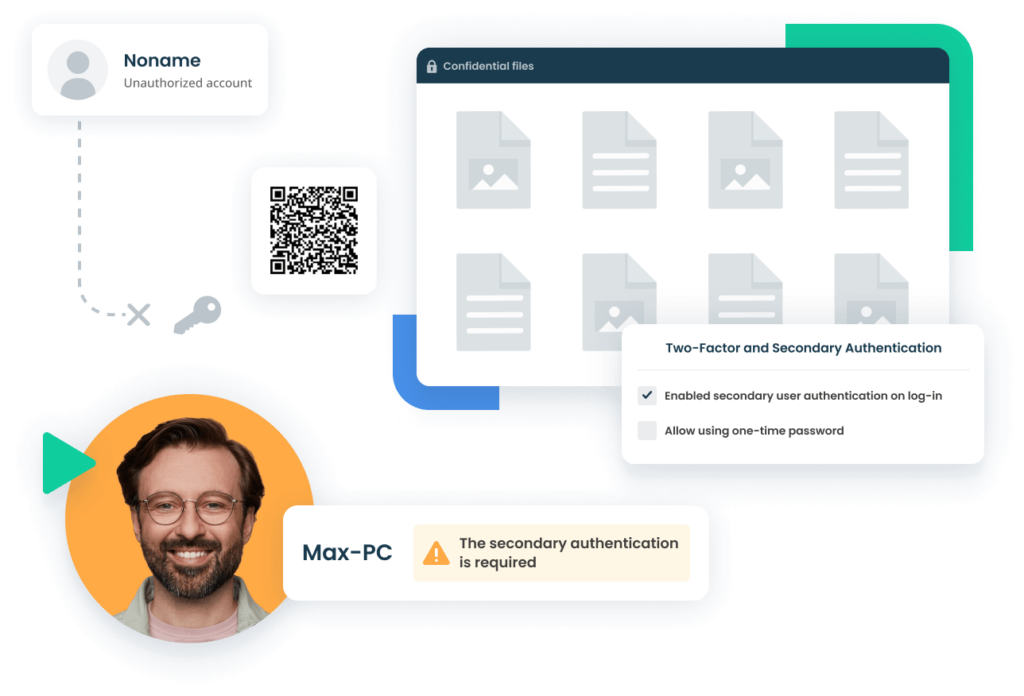
Secondary authentication to identify users of shared and built-in accounts
Gain full visibility and transparency over actions performed under generic credentials (root or admin) with the help of Syteca’s secondary authentication feature.
You can use this tool to:
- Attribute actions of faceless admins and default OS accounts to individuals
- Comply with security standards regarding unambiguous user–action attribution
- Simplify incident investigation by tracking a user’s actions across accounts
Our secondary authentication feature is available for every Syteca customer under any license.
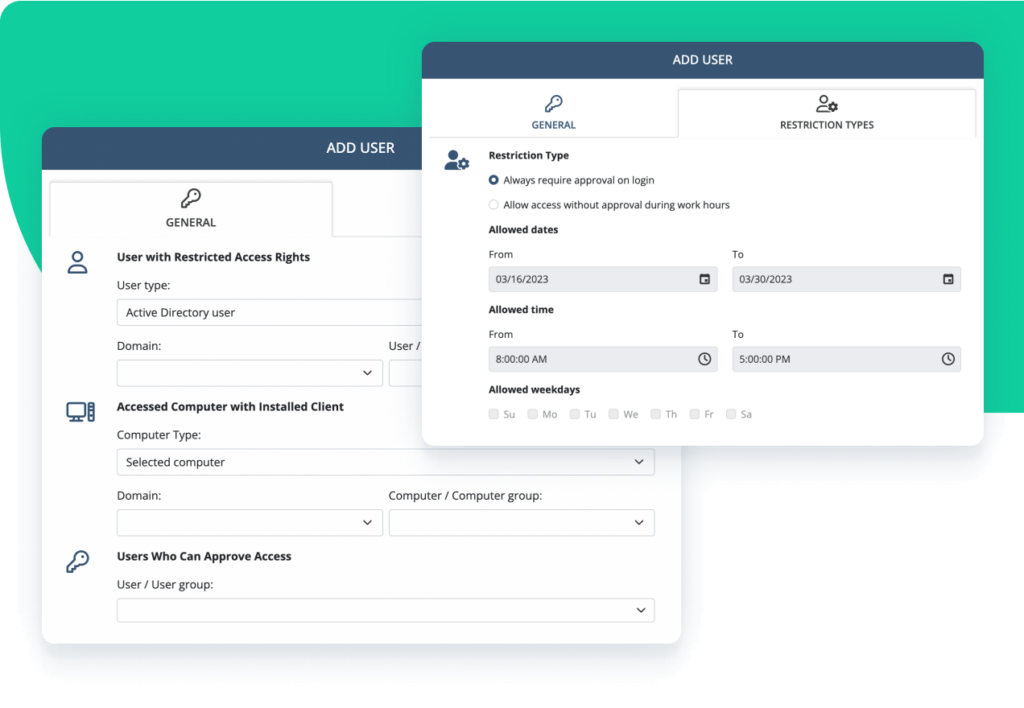
Privileged access management
Once user identity is verified, the next step is managing access permissions with Syteca access management capabilities. Secure your critical endpoints and ensure granular access by:
- Assigning, elevating, terminating, and managing access privileges
- Granting temporary access permissions by request
- Auditing privileged user activity
- Empowering real-time incident response
Syteca privileged access management (PAM) functionality includes privileged account and session management (PASM), password management, one-time passwords, ticketing system integration, and more.
Syteca ensures compliance while delivering smooth user authentication and access
All major regulations and security standards include controls dedicated to proper identity management. Syteca multi-factor authentication and secondary authentication functionality help you to meet these requirements in full, while comprehensive access management, monitoring, and activity auditing assist with other types of controls.
Syteca provides universal identity and access management solutions for today’s hybrid environments
Servers, jump servers, and desktops
Virtual and physical infrastructures
Any network architecture and hybrids
All essential features combined
Supported platforms
Syteca integrations
Syteca employee tracking software seamlessly integrates with your infrastructure, including with leading SIEM and ticketing systems.
What our clients say about Syteca’s insider threat prevention tools

Let’s get the conversation started
Contact our team to learn how our insider risk management software can safeguard your organization’s data from any risks caused by human factors. Book a call with us at a time that suits you best, and let’s explore how we can help you achieve your security goals.





