When presented with an opportunity, people who never even planned to attack your organization may turn into a severe cybersecurity threat. Forget to block a dismissed employee from accessing your system and they may steal or alter your critical data. Grant a third-party contractor excessive access to your infrastructure and they may cause a serious data breach. That’s why it’s crucial to make sure you don’t give insiders an opportunity to turn malicious.
In this article, we explore the nature of opportunistic attacks and possible motivations of the people behind them. We analyze how targeted attacks differ from common opportunistic attacks, what can be used as an opportunity to attack your organization, and how to prepare for opportunistic attacks.
What’s at the core of an opportunistic attack?
Opportunistic attackers lay low until the right opportunity presents itself.
Generally speaking, we can split all cyber attacks into two large groups:
- Targeted
- Opportunistic
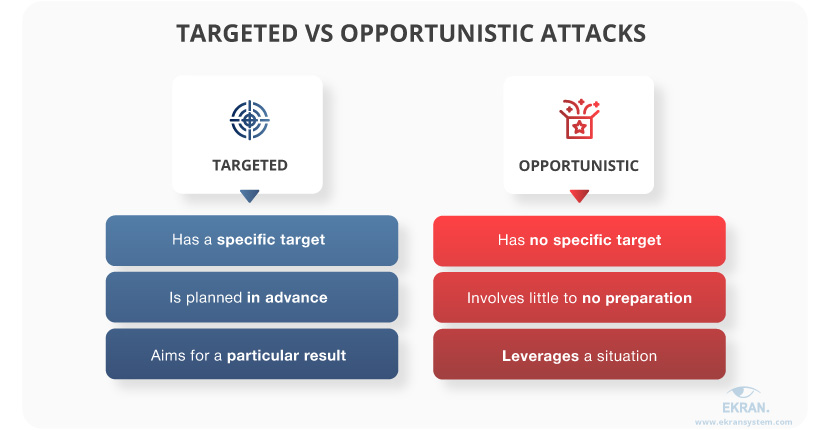
Targeted or focused attacks are usually prepared in advance, so you might notice something suspicious before it’s too late. As the name suggests, these attacks are always focused on a specific target. Malicious insiders behind a targeted attack spend time gathering information on their victim, planning their actions, and preparing for the actual attack.
For example, say a departing employee creates a backdoor account no one knows about before they leave the organization. They plan on using this account later to regain access to corporate resources and use them to their advantage. This is a classic example of a targeted attack coming from a malicious insider.
In turn, opportunistic or untargeted attacks may have no warning signs, as they are often executed spontaneously. Having no specific target, opportunistic attackers simply leverage the situation and take what they can get.
Suppose a recently terminated employee discovers they still have access to their former employer’s corporate network. After this discovery, they abuse their remaining access right to tamper with the organization’s data and services. This is a typical example of an opportunistic attack.
When an opportunistic attack originates from the outside, it’s commonly executed via malware or phishing. But with 98% of organizations feeling vulnerable to insider threats, it’s opportunistic insiders you should be aware of.
Both malicious and opportunistic insiders can have the same motivation:

Any situation enabling a user to obtain valuable data or get control over critical services without exposing their identity can be seen as an opportunity for an untargeted attack. And the scale of the damage that opportunistic attackers can cause to an organization is mostly limited by the opportunities they are presented with.
Cybersecurity Breaches Caused by Insiders: Types, Consequences, and Ways to Prevent Them
6 key factors behind opportunistic attacks
Beware of access misconfigurations and lack of visibility.
Let’s take a look at some of the most common factors that can turn a regular user into a malicious insider.
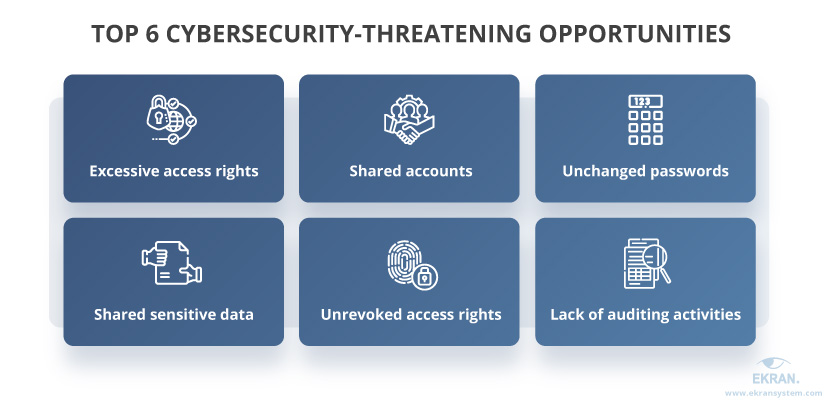
1. Excessive access rights — Misconfigured access permissions can make critical assets available to employees who are not supposed to work with them. Some employees may see this as an opportunity to tamper with these assets, either accidentally or intentionally.
2. Shared sensitive data — Coworkers tend to share all sorts of sensitive data with each other, from in-team discussions to account passwords. Some people, however, may use this knowledge to gain valuable insights on your trade secrets or execute an attack under someone else’s account.
3. Shared accounts — When different people use a single shared account, it’s usually difficult to distinguish who did what. Some people might see this lack of transparency as an opportunity to attack.
4. Unrevoked access rights — If a promoted, downgraded, or terminated employee doesn’t have their previous access permissions revoked, they can use them to their own advantage.
5. Unchanged passwords — In cases where revoking individual access is challenging, like with shared accounts, unchanged passwords allow former employees to maintain access to important services and data even after they leave your company.
6. Lack of auditing activities — Not having proper user activity monitoring and auditing routines in place creates an environment conducive to opportunistic attacks. When people know they will be caught, they are unlikely to take an opportunity even when presented with one.
Now that we’ve explored the basics of opportunistic attacks, let’s talk about ways you can protect your organization from such a threat.
Insider Threat Statistics for 2021: Facts and Figures
How to deter an opportunistic attacker?
Prevent incidents instead of handling their consequences.
The best way to deter opportunistic attackers is not to give them a chance to harm your organization in the first place.
You need to understand what sensitive information you have and who in your company has access to it. Consider running a thorough risk assessment so you can determine exactly what valuable assets need to be protected and from what risks. Once you know the most sensitive spots in your system, you can take proper precautions to ensure their protection.
Below, we specify four best practices that can help you mitigate the risk of opportunistic attacks.

1. Limit insider access to critical data. To secure your valuable assets from opportunistic insiders, try implementing these practices:
- Follow the principle of least privilege so your employees and subcontractors have the exact access permissions they need to do their job.
- Establish a clear access management policy so that every time someone in your organization changes their position or departs, their access permissions are reviewed or revoked.
- Educate your employees on data protection basics so they know exactly what information they can share with whom and to what extent.
Insider Threat Awareness: What Is It, Why Does It Matter, and How Can You Improve It?
2. Manage passwords securely. Weak and outdated passwords create additional risks for you and opportunities for malicious actors. To minimize cybersecurity risks related to credential compromise, consider the following recommendations:
- Set clear rules for password use, focusing on minimal password requirements, password rotation, and credential sharing routines. And make sure to educate your employees on these rules.
- Deploy a password management tool that will help you secure and automate password creation, rotation, and termination.
- Look at relevant compliance regulations and cybersecurity standards for additional password management guidance.
Privileged Password Policy Compliance Overview: NIST 800-63, HIPAA, PCI DSS, GDPR
3. Secure shared accounts. While it may create additional cybersecurity risks, having accounts accessed and managed by multiple users is a necessity for many organizations. If replacing shared accounts with similar individual ones is not an option for you, here’s what you can do to improve account security:
- Change passwords to shared accounts every time someone with access changes their position or leaves your organization.
- Add one more layer of user authentication so you can distinguish the actions of different users under the same account.
7 Best Practices to Prevent Intellectual Property Theft
4. Monitor and audit user activity. Deploying user activity monitoring software and performing regular internal audits can not only help you detect early signs of an insider attack but provide you with a few more benefits:
- Detect misconfigured access permissions
- Find inactive and suspicious accounts that need to be deactivated or deleted
- Find outdated passwords
- Discover reasons behind reduced employee productivity
You can also try filtering out applicants prone to opportunistic attacks when running background checks.
4 Ways to Detect and Prevent Misuse of Data
Mitigate opportunistic attacks with Syteca
While you can use separate tools for implementing these best practices, it’s better to look for a single solution that will make it easier for you to detect and deter opportunistic insiders.
Syteca is a universal insider risk management platform that provides a wide selection of features to detect, disrupt, and deter different types of insider threats. Our platform can help you gain more visibility into user activity within your network, increase the granularity of access management, and enable a timely response to cybersecurity incidents.
In particular, deploying Syteca enables you to:
- Monitor and review in real time the activity of on-site and remote employees as well as subcontractors to see who does what within your network
- Record user sessions and review them in a YouTube-like player, and use these records as evidence during audits and investigations
- Granularly manage access for separate user accounts or roles using Syteca’s privileged access management feature so your employees can access only the data and services they need
- Mitigate credential theft with multi-factor authentication
- Distinguish individual users working under shared accounts with secondary authentication
- Receive alerts and notifications on risky events and suspicious activity to enable timely incident response
- Detect and block suspicious users and processes in real time with an AI-powered user and entity behavior analytics module
- Generate reports for internal and external audits, both manually and automatically, and export them in a tamper-proof format
By leveraging all of the capabilities of Syteca, you’ll be able to effectively detect opportunistic attackers and mitigate the risks posed by malicious insiders.
7 Third-Party Security Risk Management Best Practices
Conclusion
The key difference between targeted attacks vs common opportunistic attacks is that an opportunistic hacker leverages a chance they’re presented with rather than plans their attack ahead. Any weaknesses they find in your security system can present an opportunity, from misconfigured access permissions to shared passwords and accounts.

Untargeted attacks can originate from the outside, as with opportunistic ransomware attacks, or from inside your organization, as with opportunistic insiders. To deter opportunistic attackers, you need to gain visibility across your organization’s network so you can see who accesses your critical assets, when, and what they do with them.
The Syteca platform provides you with robust access management, activity monitoring, and incident response capabilities. Request a 30-day trial of Syteca and see how you can strengthen the protection of your valuable data and systems right now.




