The Health Insurance Portability and Accountability Act (HIPAA) is a US law that establishes privacy standards for patients’ medical records and health information. It was enacted in 1996 to protect patients as well as medical institutions and healthcare providers. HIPAA defines specific rules for protecting the privacy and security of personally identifiable health information.
Complying with HIPAA is tricky, as it consists of multiple rules and regulations. But following them is vital if you want to secure your data and avoid penalties. In this article, we discuss common types of HIPAA violations, penalties that await you for breaking this law, and the best measures to ensure HIPAA compliance and the security of patient information.
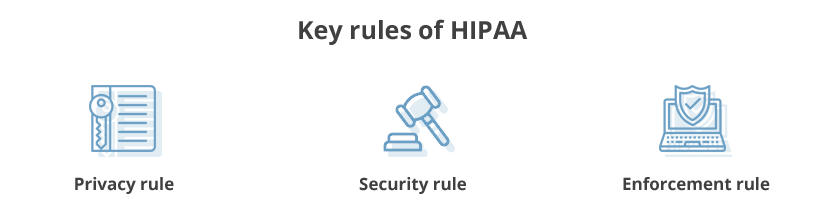
Three key HIPAA rules
HIPAA standards provide patients access to their medical records, give them control over how their personal health information is used, and determine who can view and read it.
HIPAA has three key rules that establish policies and procedures for data security:
- Privacy rule — Establishes standards for securing Protected Health Information (PHI). This rule applies to all healthcare institutions and companies who possess PHI, as well as to their business associates. The rule defines safeguards to protect the privacy of PHI and sets limits and conditions when such information may be used without authorization from a patient. The privacy rule also gives patients the right to access their own health information.
- Security rule — Extends the privacy rule by establishing standards for handling electronic Protected Health Information (ePHI). This rule defines security measures and access policies for data at rest and in transit. Similarly to the privacy rule, the security rule applies to any entity possessing ePHI.
- Enforcement rule — Sets penalties for breaking the HIPAA privacy and security rules and describes the procedures for investigations and public hearings related to data breaches that expose PHI.
There are a thousand ways to break HIPAA rules depending on the type of institution, the type of data stored, and the protection methods implemented (or not implemented). Let’s take a look at four key tiers of HIPAA violations.
Types of HIPAA violations and penalties
There are four tiers of HIPAA violations. Each carries a certain type of financial penalty. Knowingly violating HIPAA rules can also lead to criminal charges resulting in jail sentences.
In April 2019, HIPAA significantly lowered the maximum amount of penalties for three tiers of violations. Previously, the annual limit for each tier was $1.5 million. The current legislation lists the following HIPAA violation fines:
- Tier 1 — An entity (an organization or an individual) didn’t know about the data breach. If you broke HIPAA rules unintentionally and can prove you were unaware of the violation, the civil penalty for unknowingly violating the law is $100 to $50,000 per violation. The maximum annual limit is $25,000.
- Tier 2 — An entity knew about the violation but had a reasonable cause to neglect HIPAA rules. In this case, the penalty is $1,000 to $50,000 per violation. The maximum annual limit is $100,000.
- Tier 3 — An entity willfully neglected the violation but corrected it within 30 days after its discovery. In this case, the penalty is $10,000 to $50,000 per violation. The maximum annual limit is $250,000.
- Tier 4 — An entity knew about the violation, willfully neglected it, and didn’t fix it in time. This type of violation is punishable with a penalty of $50,000 per incident. The maximum annual limit for tier 4 violations is $1.5 million. Cases of exceptional security neglect that have a severe impact may result in criminal charges in addition to civil penalties.
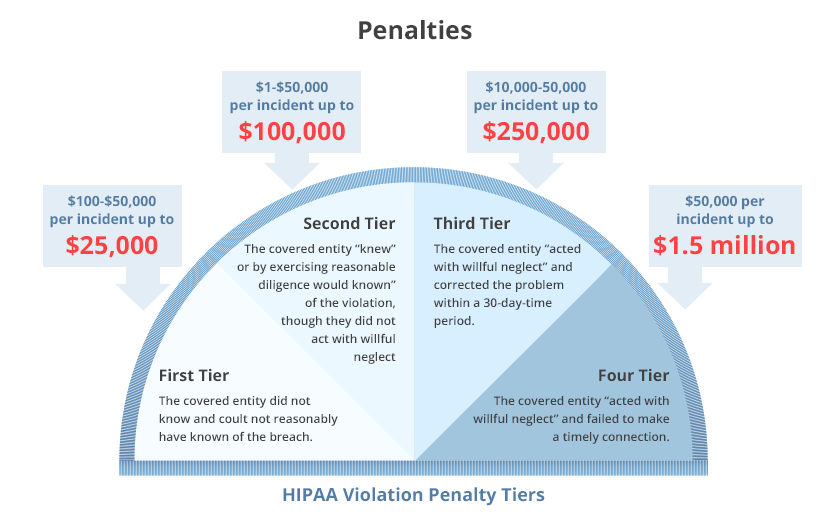
As you can see, Tiers 1–3 have a gradation of penalties for noncompliance with HIPAA. If an entity can prove that it didn’t know of the violation or had a reason not to fix it, they can avoid major penalties. It’s up to the Office for Civil Rights (OCR) to determine a financial penalty within the appropriate range.
The OCR considers a number of factors when determining penalties, such as:
- The length of time the violation was allowed to persist
- The number of people affected
- The nature of the data exposed
- The entity’s willingness to assist OCR in the investigation
- Prior history of violations
- The entity’s financial condition
- The amount of harm caused by the violation
How to protect medical data
Healthcare is one of the most breached industries according to the 2019 Data Breach Investigations Report by Verizon. Healthcare organizations were the subjects of 15% of all data breaches in 2018, and 59% of these breaches were caused by internal actors.
Due to the high value of personal records, healthcare breaches also result in the highest average cost per breach — $6.45 million according to the 2019 Cost of a Data Breach Report by the Ponemon Institute. And these numbers keep rising year over year.
5 Industries Most at Risk of Data Breaches
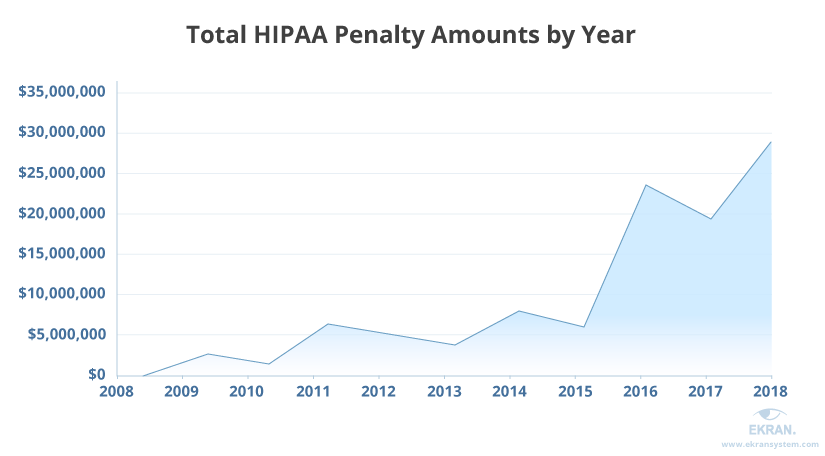
HIPAA penalties are rising, too. In 2018, the OCR received the largest amount in penalties ever — more than $28 million. It also received the largest ever settlement from a single entity. The health insurance company Anthem paid $16 million as a result of its 2015 data breach, in which the PHI of 78.8 million Anthem clients was stolen by hackers. Anthem also paid $115 million to its clients.
The HIPAA Guide defines the nine most common causes of data breaches that happen because healthcare entities have failed HIPAA compliance:
- Professional hacker attack
- Business associate disclosure
- Incorrect admin procedures
- Insufficient IT security measures
- Unauthorized access
- Employee dishonesty
- Lost or stolen devices
- Accidental PHI disclosure by an employee
- Improper disposal of data
As you can see, most breaches happen because of a lack of security measures and malicious or inadvertent employee activity.
So what’s the best way to protect your data?
HIPAA enforces three sets of safeguards that keep PHI from getting into the wrong hands. Let’s take a look at them:

Administrative safeguards define a set of actions, procedures, and policies you need to implement within your organization. They include:
- Establishing a security management process
- Creating risk analysis, management, and mitigation procedures
- Implementing an insider threat protection program
- Appointing people responsible for handling data breaches
- Increasing security awareness
- Conducting a periodic review of implemented measures
At first, these requirements may seem like paper pushing. But in fact, administrative measures help to establish continuous security practices. They also define how your employees have to act when they discover a data breach. When it happens, there’s not a moment to waste, and an agreed plan of action helps to save precious time.

Physical safeguards concentrate on securing physical access to PHI. Physical safeguards describe measures that should be implemented in offices and institutions that store hard copies of PHI. They also define policies for workstations:
- Workstation security. Workstations have to be protected from unauthorized access, both physically and digitally. You can choose any security measure you like to ensure the security of workstations, from controlling and limiting user access to storing critical data in a physical safe.
- Workstation use. Each workstation, whether in-house or remote (including those of third-party companies and subcontractors) has to be protected with strong credentials, antivirus software, a firewall, and other cybersecurity measures.
Technical safeguards refer only to ePHI. This set of safeguards focuses on the following measures:
- Access control. The list of individuals (or job titles) with rights to read, write, or edit ePHI should be strictly limited. You should have the means to establish and control the level of access for each user, both in-house and remote.
- Authentication. You need to verify that a person trying to access data has a right to do it.
- Audit control. Internal audits and incident investigations help you adjust your cybersecurity policies to meet new threats. You should also implement a tool to record any activities with ePHI — for example, a monitoring system.
It’s easy to comply with these technical safeguards with the help of Syteca. Our insider threat protection platform provides you with these features:
- Identity management for preventing unauthorized access to your data and distinguishing users of shared accounts. This is achieved using multifactor authentication and one-time passwords.
- Access management for controlling access to critical data and endpoints. With privileged account and session management, integration with ticketing and SIEM systems, and manual login approval, you can ensure granular access control.
- User activity monitoring for keeping track of every action inside your system. Sytecasaves captured data as video and audio records. Indexed search by multiple parameters allows you to trace any activity, establish its context, and determine the true intent of a user.
- Third-party monitoring for enforcing continuous monitoring, identity verification, and remote access management for vendors like MSPs and IT outsourcing services.
- Reporting and investigating for collecting data on security incidents and violations, analyzing that data, and perfecting your cybersecurity policies. Also, you can export data in a protected file for forensic activities.
HIPAA Compliance Password Policy
Conclusion
HIPAA is a complex law that regulates the storage, transmission, and use of health data. HIPAA fines for violations may be substantial, and they are progressive. This means a company will get a penalty each month and each year until the security weakness is fixed. Also, a data breach causes severe reputational damage for any healthcare institution.
Syteca can be used as a HIPAA compliance solution that can help you meet HIPAA requirements and avoid penalties. Our platform provides all the tools you need to ensure the safety of ePHI: user activity monitoring, access control, third-party monitoring, and tools for audits and investigations.
Healthcare Organization Ensures HIPAA Compliance and Efficient Remote Work with Syteca [PDF]
Syteca is also equipped with powerful identity management functionality, built according to NIST standards. Coupled with real-time alerts and notifications on cybersecurity incidents, Syteca will protect you from data breaches.




