The third quarter of 2022 was challenging for government and corporate servers across the globe — we witnessed a 70% increase in data breaches over the second quarter’s numbers. Considering that security lapses are mainly on the shoulders of CISOs, it’s vital to know the instruments for improving their effectiveness.
This blog post outlines a white paper written by former Gartner analyst Jonathan Care. Download the white paper for more comprehensive first-hand insights on CISO best practices, rising trends, and upcoming technologies that will enhance CISO effectiveness in 2023.
Roadmap to CISO Effectiveness: White Paper Summary
As a recognized expert in the field of cybersecurity and fraud detection, Jonathan Care gives the following tips on improving CISO effectiveness:
1. Gauge risk appetite without muddling authority
The role of CISO is associated with burnout and stress. The Heidrick & Struggles CISO Survey shows that less than half of CISOs want to remain in the role, citing stress as their primary concern.
Collaboration with senior colleagues is crucial when defining risk appetite. However, CISOs frequently find themselves alone when it comes to enforcing policies, making complex decisions, and taking responsibility for any resulting security lapses.
Giving CISOs more control is one of the key tips on how to improve CISO effectiveness and reduce stress.
2. Adopt an identity-first networking model
As zero trust networking is not a universal solution, an effective security program for CISOs should consider alternatives that complement advanced identity management systems and customer data anonymization.
Giving a third-party provider power to establish identities may seem counterintuitive at first. But it makes sense if you consider that user identity is the core of Microsoft’s and Google’s business models.
Tying user identity directly to the domain name server (DNS) makes identity forging difficult and strengthens network security. You can also adjust the specific authentication information requested from the identity service provider to maximize client protection and compliance with legal requirements.
Rethinking IAM: What Continuous Authentication Is and How It Works
3. Effectively manage insider risk
Insider data breaches have become more expensive and difficult to contain, with the risk of an insider data breach increasing by 44% since the pandemic.
Overreacting to the situation by forcing remote workers into the office enhances physical access opportunities that may lead to malicious insider incidents, while a free-for-all policy can result in carelessness and credential theft.
To fight insider risks, CISOs in 2023 will implement a defense-in-depth strategy and deploy insider risk management software such as Syteca.

4. Incorporate a password checkout system
As cyber threats continue to evolve, CISOs are seeking innovative ways to enhance password protection. One solution gaining traction is a password checkout system, which prevents more than one user from accessing any specific account or secret at the same time.
Password checkout makes secret assets exclusive. That means any attacks that rely on simultaneous logins simply will not work.
Combined with automatic password rotation and privileged access management services, which Syteca also provides, password checkout functionality makes it much more difficult to steal a password. While password checkout may not be appropriate for all secrets, CISOs should consider this tool to bolster their organization’s cybersecurity in 2023.
Privileged Access Management: Essential and Advanced Practices
5. Increase data anonymity capabilities
Privacy concerns stopped many organizations from outsourcing critical security tasks in response to a rise in cybercrime. Anonymizing data — one of the data security best practices for CISOs — helps you protect sensitive data when conducting investigations and outsourcing HR- and security-related tasks.
Syteca offers anonymization capabilities for internal cyber fraud investigations. The data anonymizer in Syteca uses numbers and investigation target IDs instead of real names and data. This allows your organization to treat users without bias and bring in outside experts.
5 Reasons to Start Pseudonymizing Personal Data in Your Organization
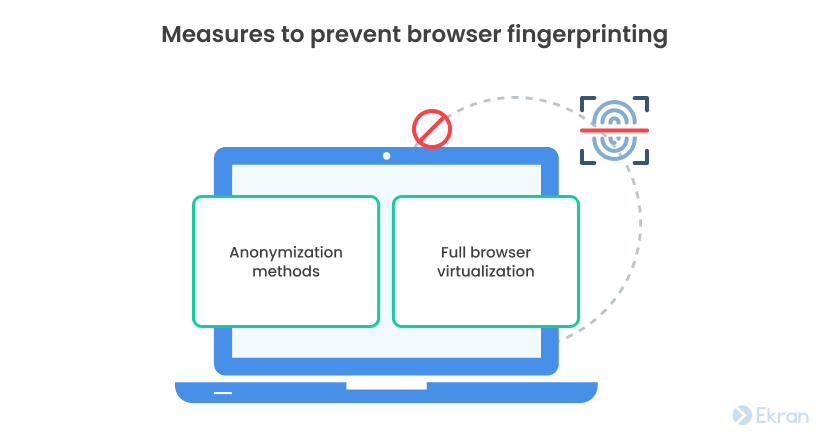
6. Defend employees against browser fingerprinting
Browser fingerprinting is becoming a significant cybersecurity concern as hackers use it more frequently to track user identities.
A fingerprinted user is much more vulnerable to spear phishing, identity impersonation, and social engineering attacks. Browser fingerprinting can bypass VPNs, Onion routing, and similar multi-node anonymous communication techniques.
CISOs implementing anti-fingerprinting measures will be more effective at protecting their organizations. These measures include:
7. Crack down on AI poisoning
Researching the topic of AI poisoning and looking for how a CISO can effectively manage the related risks is among the best practices for CISO effectiveness in 2023.
AI poisoning is an ongoing trend in which artificial intelligence (AI) and machine learning (ML) ingestion streams are intentionally sabotaged. By exploiting interactional capabilities of AI, hackers may poison neural networks with wrong information or intentions. The results of this exploitation may range from racist chat bots to confidentiality attacks.
AI poisoning is expected to be a major cybersecurity issue in 2023 for organizations that use AI or ML services, which puts the responsibility on the CISO. Even if your company doesn’t use AI, many of the services you employ probably do.
10 Must-Have Information Security Policies for Every Organization
8. Comply with new government cybersecurity requirements
New US and UK government cybersecurity requirements established during the pandemic will come into effect in early 2023. The CISO’s job is to determine which requirements apply to their business and work on achieving full compliance.
US organizations will have to consider Executive Order 14028, which will force manufacturers to inform customers of products created with greater consideration of cybersecurity risks and capabilities.
The UK has also published new standards for cybersecurity in educational institutions. They will apply to network software and devices and require audits and compliance with disaster recovery rules.
Using dedicated solutions like Syteca can help CISOs ensure their organizations meet cybersecurity compliance requirements.
Healthcare Organization Ensures HIPAA Compliance and Efficient Remote Work with Syteca [PDF]
Conclusion
To be effective, CISOs have to manage their stress levels and implement vital data protection measures. The latter include adopting an identity-first networking model, managing insider risks, and anonymizing data. CISO best practices for information security involve focusing on threats like AI poisoning and browser fingerprinting and taking measures to ensure organizations’ IT compliance.
A CISO’s efforts won’t be effective without dedicated cybersecurity solutions. As an all-in-one insider risk management platform, Syteca can help CISOs protect sensitive assets from human-related security risks.
For more thoughts on stress and the role of a CISO’s mental health, download the complete white paper — Roadmap to CISO Effectiveness.
Written by former Gartner analyst and recognized cybersecurity expert Jonathan Care, the white paper contains useful first-hand insights and provides a complete description of all best practices for CISOs and data protection measures outlined in this blog post.




