Today’s banks and financial institutions closely cooperate with various third-party vendors. While such cooperation brings a lot of benefits, it also raises some significant concerns regarding the security of the data and resources these vendors have access to. In fact, according to Verizon’s 2019 Data Breach Investigations Report, the financial sector is among the most targeted, accounting for about 10% of all data breaches across all industries in 2018.
In this article, we discuss the key reasons why financial institutions hire independent contractors and what cybersecurity risks it exposes them to. We also explore how building a third-party vendor risk management program can help you mitigate these risks.
Why do banks hire third-party vendors?
It’s not only about saving money.
Banks and financial institutions can outsource all kinds of operational activities, from accounting and appraisals to marketing and even loan servicing. Working with independent subcontractors brings multiple benefits:
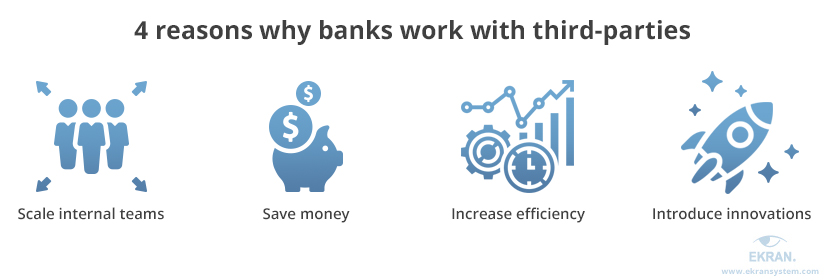
Let’s take a closer look at these reasons.
Increased flexibility and scalability of internal teams. Hiring third-party vendors gives financial institutions the freedom to scale their internal teams the way they want. When faced with a new task, companies traditionally would need to recruit a new specialist. With third-party vendors, a subcontractor can meet their needs.
Cut costs, especially on recruitment. Head hunting is costly and time-consuming, and it isn’t always successful. Additionally, working with third parties may help an organization save some money on taxes.
Increase efficiency. Delegating some tasks to third-party vendors allows financial institutions to work more efficiently: process more operations, serve more customers, and so on.
Introduce new technologies and solutions. Working with third-party vendors is a great way to deploy new, game-changing solutions with minimal risks. Organizations can leave the processes of choosing, testing, and evaluating solutions to subcontractors and move straight to the implementation stage.
Despite all these advantages, many banking organizations are wary of hiring independent contractors, mostly because of the security and compliance issues it entails. In the next section, we take a closer look at the key challenges and risks that financial institutions face when working with subcontractors.
Third-Party Providers – Managing Insider Risks
Cybersecurity risks of third-party services
Your ally may easily become your biggest threat.
Banks often have to grant third parties access to sensitive data, critical systems, and other important resources. This is perhaps the biggest risk of cooperating with subcontractors. After all, there’s no guarantee that your third-party vendor won’t misuse their access privileges. Additionally, hackers may target your subcontractors to get access to your sensitive data and critical systems.
It’s crucial to remember that while you may delegate some tasks and functions to a third party, ensuring your organization’s cybersecurity is still your own responsibility. Neglecting this responsibility may lead to devastating consequences. In the past few years, we’ve seen plenty of proof:
- In April 2017, a subcontractor uploaded a database with personal information of 20,000 customers of Scottrade Bank to unprotected cloud storage. Bank representatives stated that the leak was the result of human error on the subcontractor’s side and that the bank’s own systems weren’t affected.
- In July 2017, hackers used a third-party vendor to attack Italian bank UniCredit. The bank actually suffered two attacks in ten months — the first in autumn 2016, the second in summer 2017. As a result of these attacks, nearly 400,000 customer loan accounts were exposed, containing personal information and banking details.
- In December 2018, cybercriminals attacked the European Central Bank’s website hosted by a third-party provider. The attack remained unnoticed for several months. According to official statements, there was a risk of data leaks due to malware injected by the attackers.
- In January 2019, several US banks and financial firms suffered a serious data leak due to a third-party vendor’s mistake: a server where Ascension stored digital versions of paper financial documents was misconfigured. As a result, anyone could get access to a database with over 24 million credit reports containing sensitive customer information.
Recognizing the danger that third parties may pose to cybersecurity in the financial sector, regulatory authorities pay special attention to the problem of third-party cyber risk management. In particular, managing third-party vendor risks in one of the key requirements of the Risk Management Guidance bulletin released in 2013 by the US Office of the Comptroller of the Currency (OCC).
So what are the risks posed by third-party vendors?
As the cases we’ve described show, third parties aren’t necessarily the villains. Cybercriminals often target subcontractors of larger organizations.
Let’s take a look at six key cybersecurity concerns regarding cooperation with third-party vendors:
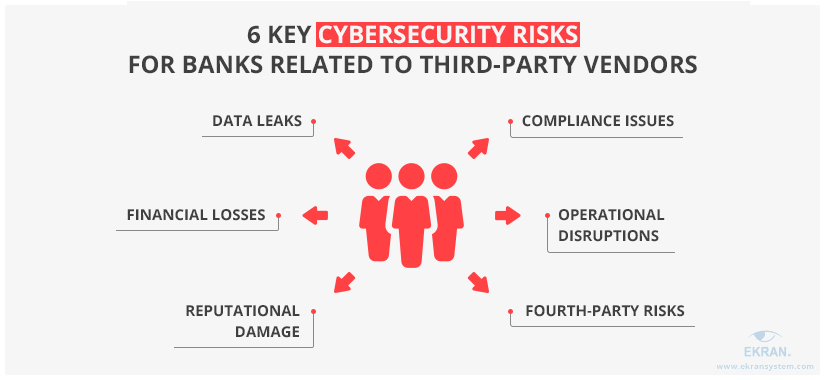
Data leaks. Information is a financial institution’s most valuable asset, and it can be targeted by cybercriminals or be damaged due to human errors.
Financial consequences. Data breaches often lead to regulatory penalties or lawsuits from customers. Additionally, affected banks have to conduct security audits, digital forensic investigations, and cybersecurity remediations after an incident.
Reputational damage. Third-party-related security incidents may harm a bank’s reputation and lead to loss of customer trust.
Compliance issues. Financial institutions have to comply with financial data security regulations and standards: OCC bulletins, GLBA, PCI DSS, NIST, etc. Failure to comply will result in fines and penalties.
Operational disruptions. Cybersecurity incidents caused by third-party vendors may seriously disrupt your company’s operations and affect the availability of your network and services.
Fourth-party risks. Who said that your third parties can’t have third parties of their own? Make sure that your subcontractors won’t re-outsource any of your critical services to so-called fourth parties. You can do this by adding a corresponding clause to your contract.
The good news is that you can successfully mitigate these risks by implementing a thorough third-party risk management (TPRM) program. In the next section, we give you a step-by-step guide to building one.
Banking and Financial Cyber Security Compliance
Building a third-party risk management program
Prevention is always better than cure.
Third-party risk management is a complex process of analyzing and addressing the risks associated with subcontractors. OCC Bulletin 2013-29 outlines five key stages of the third-party risk management lifecycle:
- Planning. Build a thorough plan for managing relationships with third parties. This plan should take into account the complexity and the level of risk posed by relationships with particular subcontractors.
- Due diligence. Validate your third parties and make sure they have the necessary level of cybersecurity and financial stability to provide your organization with the required services or products.
- Contract negotiation. Compose and negotiate a contract that clearly specifies who’s responsible for what and what rights each side has.
- Monitoring. Once the contract is signed, ensure ongoing monitoring of the third party’s activities.
- Oversight and accountability. Senior management is responsible for establishing proper risk management regarding cooperation with third parties.
A third-party risk management program for financial institutions is a necessary element of effective subcontractor management. Such a program is a set of policies, tools, and activities for managing the risks posed by third-party vendors. Implementing a comprehensive third-party vendor management program helps you see the big picture and be ready to efficiently deal with various cybersecurity incidents related to third parties.
Below, we list the key benefits of implementing a TPRM program.
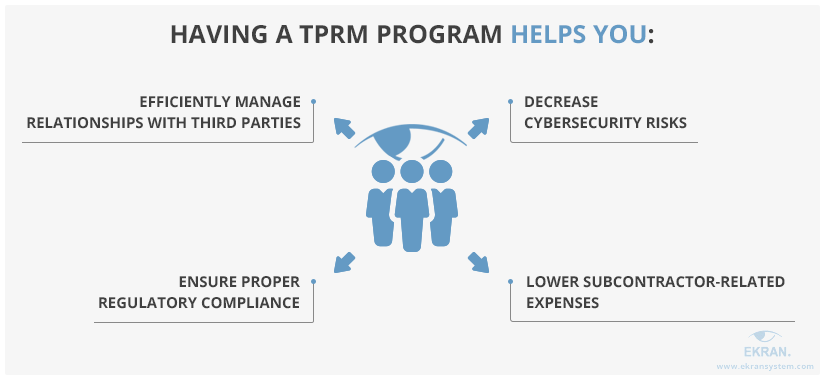
To build your own TPRM program, you can start with the following third-party risk management best practices:
Appoint responsible personnel. Choose a dedicated individual or create a team responsible for monitoring subcontractors and managing third-party vendor cybersecurity risks.
Clarify key regulatory requirements. To efficiently manage third-party vendors, you need to know what regulatory requirements your organization is subject to and what guidelines and recommendations it intends to follow. Start with the documents and regulations we already mentioned: OCC bulletins, PCI DSS, NIST, BSA. Also, make sure that your third parties know what cybersecurity standards, laws, and regulations you must comply with. They should include these requirements in their own regulatory compliance programs.
Outline possible risks. Analyze known subcontractor-related cybersecurity incidents to compose a list of possible threat vectors and risks. Look for the most efficient ways to address each of these risks and prevent and respond to potential incidents. Include these activities in your TPRM and incident response programs.
Build a risk profile for every subcontractor. You need to know what risks are entailed by cooperation with each of your third-party vendors. When building a vendor profile, take into account such factors as:
- Systems, services, data, and physical locations the vendor has access to
- Levels of access privileges granted to this vendor
- The state of the vendor’s cybersecurity program
Using such profiles, you can easily determine what vendors should be monitored more closely.
Use third-party vendor risk management software. Deploying additional tools, such as remote computer monitoring software, can help you improve the efficiency of your third-party vendor risk management. Pay special attention to third-party vendor monitoring solutions that allow you to set granular access permissions, add more layers of protection to the most critical assets, and monitor a subcontractor’s actions within your network.
Incident Response Planning Guideline for 2019
Mitigate third-party risks with Syteca
Syteca is an ultimate platform for managing third-party cybersecurity risks.
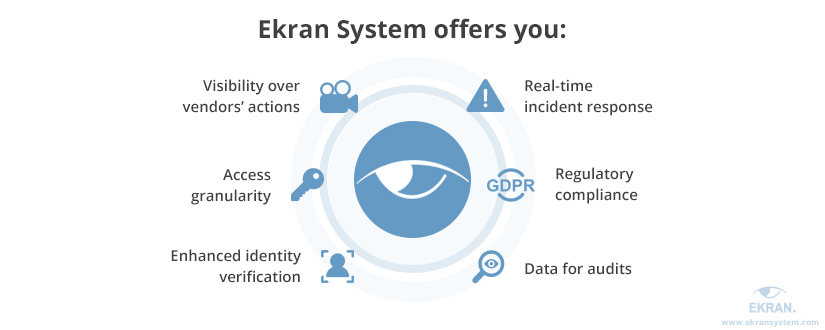
Let’s see how you can get all these benefits with one easy-to-use solution.
- Syteca enables continuous monitoring of a third-party vendor’s activity and records all types of user sessions, including Remote Desktop Protocol (RDP) sessions, in a comprehensive video format. Video is coupled with audio records and indexed with metadata such as keywords, visited URLs, and names of opened files and applications. You can use these records later for analyzing your subcontractor’s activity and investigating cybersecurity incidents.
- Syteca’s privileged access management feature allows you to set granular access permissions for different roles and accounts. As a result, you can make sure that a specific system or endpoint can only be accessed by a limited circle of people and can limit the time for which such access is granted.
- To improve the protection of your most critical assets, you may use additional features such as two-factor authentication, manual access approval, one-time passwords, and secondary authentication.
- A robust alerts and notification system will help you respond to any cybersecurity incident in real time. You can create custom alerts and set an automatic response to specified events. In particular, you can configure Syteca to block suspicious users and terminate suspicious sessions or processes.
- Syteca helps organizations comply with financial data security regulations and standards such as NIST, PCI DSS, GLBA, and SOX. This platform provides tools and functionalities for ensuring user activity monitoring, access management, and cybersecurity audits.
- Sytecaallows you to configure detailed reports based on customized parameters, including captured keystrokes, visited URLs, and user activities recorded outside of work hours. These reports can be exported in a comprehensive forensic format for further audit and analysis.
Syteca’s Third-Party Security Monitoring Solutions
Conclusion
Working with third parties brings a lot of benefits to banks, from saving money on taxes to improving the quality of their services. However, third-party vendors often have privileged access to critical assets of their clients, and financial institutions have limited abilities to control the way these privileges are used.
This is why addressing cybersecurity risks associated with subcontractors is vital for banks and other financial institutions. Building an effective third-party vendor risk management program can help institutions clearly define the risks they face when working with third parties as well as the most effective ways to mitigate them.
Syteca is an insider threat prevention platform that comes with a set of useful features for effective third-party vendor management. Our platform allows you to monitor user activity, manage privileged access, and respond to cybersecurity events in real time. Take the first step towards enhancing the cybersecurity of your organization — download a trial version of Syteca today.
Privileged User Monitoring and Auditing for a US-Based Financial Services Company [PDF]




